
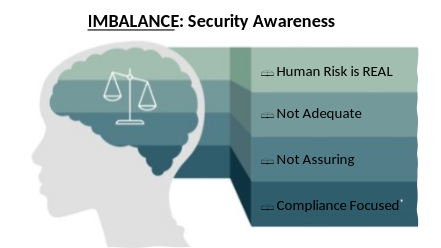
Problem Statement: Human risk is real, and information and cybersecurity awareness trainings are not assuring and adequate. Period.
Often security trainings are compliance-focused, as against assurance-focused. Agree?
By Ashish Paliwal, Information Security Officer, Sony
Scare Tactic
Email scams related to COVID-19 surged 667% in March 2020 alone. Users are now three times more likely to click on pandemic-related phishing scams. Furthermore, 90% of newly created Coronavirus Domains are scammy with a 2000% increase in malicious files with “Zoom” in name as an example. Going back a bit, data breaches exposed 4.1 billion records in the first six months of 2019 globally; and 76% of businesses reported being a victim of a phishing attack in the same year.
Studies
- Leron Zinatullin, a security researcher, in his book titled The Psychology of Information Security published in 2016 refers to below common reasons for non-compliance:
- No clear reason to comply
- Cost of compliance too HIGH
- Inability of compliance
- Iacovos Kirlappos, Adam Beautement, and M. Angela Sasse‘s research report published in 2013 on “Security-Awareness Principal Agents” abandons the traditional
“command-and-control” approach which mostly comprises of a long list of do’s and don’ts often as part of “annual security training” which has little to no effect on security behaviors. - Furthermore, research on “Susceptibility to Persuasion” by the University of Cambridge, endorses a similar school of thought, consisting of 10 broad categories with each to have proven in the past to have some connection with individuals being persuaded to do something; like respond to an advert or change their usual behavior slightly.
Ref: Susceptibility to persuasion (i.e. persuadability) is a phenomenon of the subject who is persuaded, but is influenced by the plausibility of the story of which they are persuaded.
Also, refer to the Persuasion Techniques (below) published by Dr. BJ Forgg, Director of Behavior Design Lab @ Stanford University.
- Principle of reciprocation: People feel obligated to return a favor.
- Principle of scarcity: When something is scarce, people will value it more.
- Principle of authority: When a request is made by a legitimate authority, people are inclined to follow/believe the request.
- Principle of commitment and consistency: People do as they told they would.
- Principle of consensus: People do as other people do.
- Principle of liking: We say “yes” to people we like.
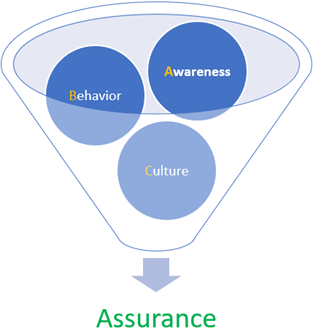
- Lastly, an article titled “Awareness Isn’t Enough” published by Jinan Budge, Principal Analyst @ Forrester also endorses influencing behavior by explicitly calling out the ABC of Security (Awareness, Behavior, and Culture). I suggest attempting drawing assurances from these.
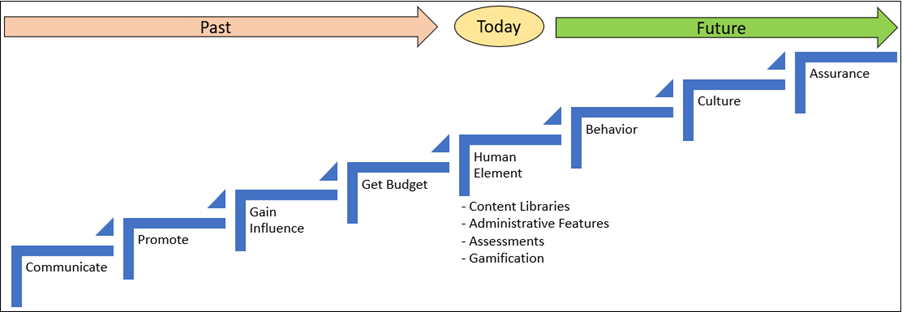
Proposal
Build a “control ecosystem” by tying together psychological and behavioral traits influencing “security” decisions, to positively impact and pre-empt the same via Plan A and/or Plan B.
Plan A
- Psychometric test with emphasis on the overlap of security traits with that of personality influencing any positive and/or negative behavior
- Venturing beyond security trainings into areas of behavioral modeling
Plan B
Introduction of the concept of Security Behaviour Reflection (SBR) Score
What is SBR Score all about?
- At the start of the year, all in the organization are assigned or start with say 100 points or $1000 (for example.)
- Penalize negative behaviors via deduction of points/$ (E.g. For phishing cases, -10 points for clicking, +10 for reporting, and -5 in case of no action. For data leakage, -25 points; etc.)
- Urge managers to consider SBR Scorecard for promotion and/or appraisal decisions
- Managers of reportees with maximum or minimum scorers to be rewarded and/or trained in accordance.
POC/Test Results
For testing/learning via a very small sample set, leveraged Cattell’s 16 PF (Personality Factors) survey (https://openpsychometrics.org/tests/16PF.php).
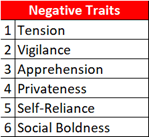
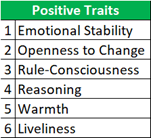
Meaning, correlations can be drawn between negative security behaviors and high tension, lower vigilance, and apprehensions. And, emotionally stable, rule conscious, and rational employees are more likely to exhibit positive security behavior.
Learnings
- Reassurance on behavioral aspects influencing security decisions
- Aligning approach to focus on positive and negative traits complementing organizational/industry context and culture
Benefits
- Endorsing Security Culture
- Threat Landscape Reduction
- Data Security
- Client Confidence ($)
Challenges
- Psychometric tests are ‘point-in-time’ indicators, and not 100% fool-proof
- $ aspect
- Psychometric tests are charged on ‘per-test’ basis
- # of psychometric required can be high depending on the size of your org
- Addressing the ‘privacy’ aspect before initiating psychometric tests (explicitly or implicitly)
- For SBR scoring, heavy reliance on allied teams (like incident management team, team managing and floating anti-phishing campaigns, etc.) with effective false-positive validations and considerations.
Work Arounds
- Create psychometrics tests in-house with a best-effort-basis algorithm
- Review onboarding (HR) policy for inclusion of ‘permissions’ for running psychometric tests
Recommendation / Way Forward: Engage!
- Consider conducting psychometric tests for new-joiners and information and cybersecurity offenders. These tests can also be tailored to fit the organizational context and culture.
- Next, Structured Cognitive Behavioral Trainings (SCBT) can be imparted in addition to regular infosec trainings.
- Consider introduction of the concept of Security Behavior Reflection (SBR) Scores at an enterprise level.
Meanwhile, stay safe and stay psyched about security!
About the Author
 Ashish Paliwal is a security innovator and change agent with extensive information security, risk, and infrastructure management expertise of 12+ years while translating evolving industry risks into ambitious technology roadmaps and robust security programs.
Ashish Paliwal is a security innovator and change agent with extensive information security, risk, and infrastructure management expertise of 12+ years while translating evolving industry risks into ambitious technology roadmaps and robust security programs.
Disclaimer
Views expressed in this article are personal. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.










