The History of Security and the Fight to Protect Ourselves
While almost everyone in modern industry has heard and thought about cyberattacks, breaches, data compromises and defenses, cyber warfare pre-dates the modern computing era....
Xiaomi Security Camera Bug Shows Other Homes’ Camera Feeds
Internet of Things (IoT) may enhance our connected lifestyle, but it has also created new attack vectors for hackers. Several security pros cautioned earlier...
Vulnerability Found in TP-Link’s Archer Routers, Now Fixed
TP-Link’s Archer Router series which is capable of handling high-speed online traffic had a vulnerability that if exploited, could allow hackers to bypass the...
Researcher Finds 5 Malicious Adware Apps on Play Store
Does that tiny Ad pop-up on the screen annoy you? Yes, we are talking about the same pop-up that no matter which app you...
Thief Stole Payroll Data of 29,000 Facebook Employees
Some tens of thousands of current and former Facebook employees are impacted after a thief stole corporate hard drives from an employee’s car. According...
Amazon’s Blink Smart Security Cameras Vulnerable to Attacks
Researchers from vulnerability detection firm Tenable discovered seven critical vulnerabilities in Amazon-owned Blink XT2 security camera systems. If exploited, the vulnerabilities could allow hackers...
Wearable Tablet Prone to a Cyber-Attack?
Deny or accept, but technology has always been a part of our lives and now it’s almost become one with our bodies too. Wearables...
The Future of Endpoint Management is Cognitive
By Vaidyanathan Iyer, Security Software Leader, IBM India/South Asia
Today, the biggest test chief information security officers (CISOs) face is to find the perfect balance...
Around 61 percent Malware ads Target Windows OS: Devcon
Security researchers revealed that most Malvertising campaigns (malicious ads) target the Windows platform more often than any other operating system.
According to the analysis by...
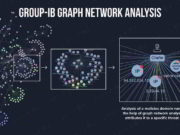
This Tool Predicts Cybercriminal Activity Even Before It Happens
Group-IB, an international cybersecurity company that specializes in preventing cyberattacks, has launched a new tool for clients, which helps to predict and attribute attacks,...