
Security services provider Quick Heal Security Labs recently uncovered a password stealing malware codenamed as “Agent Tesla” being distributed via malicious campaigns. It is said that attackers are spreading the malware via COVID-19 themed phishing campaigns to steal sensitive data by capturing keystrokes, taking screenshots, and dumping browser passwords.
Quick Heal stated that hackers are currently abusing MS Office vulnerabilities, titled CVE-2017-11882 and CVE-2017-8570, as well as archives with double extension executable (ZIP, RAR etc.).
The CVE-2017-11882 vulnerability allows attackers to run an arbitrary code to deliver the Agent Tesla malware payload. Another vulnerability CVE-2017-8570 triggers the execution of scripts without user interaction. CVE-2017-8750 downloads the .NET payload which steal sensitive data, log user keys, and send data to the SMTP server.
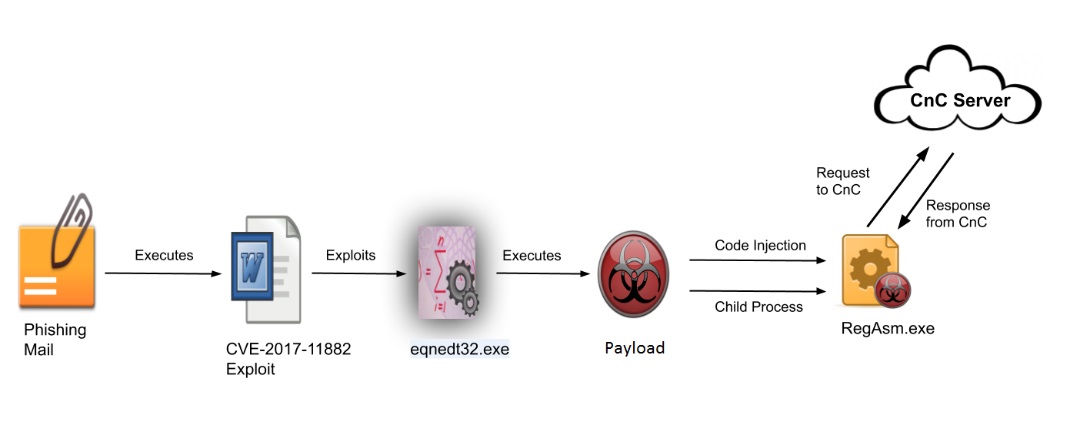
Explaining the attack vector, the researchers at Quick Heal said, “A victim receives a phishing mail with an attachment titled as ‘COVID 19 NEW ORDER FACE MASKS.doc.rtf’. This doc is an RTF file that exploits CVE-2017-11882 which is a stack-based buffer overflow vulnerability present in the Microsoft Equation editor tool. This vulnerability allows the attacker to run arbitrary code and after successful exploitation to deliver the Agent Tesla payload. This dropped payload performs code injection in known windows process RegAsm.exe. The injected code in RegAsm.exe performs all info-stealing activity and sends it to the CnC server.”
“Actors behind these campaigns are capitalizing on the global Coronavirus panic to distribute Agent Tesla malware and steal sensitive user information. Quick Heal advises users to exercise ample caution and avoid opening attachments & clicking on web links in unsolicited emails. Users should also keep their Operating System updated and have a full-fledged security solution installed on all devices,” Quick Heal added.










