
Chinese state-actor hacker groups launched attacks on ten Indian power sector companies and two seaports since early last year. The latest attack occurred on February 28, which is attributed to the Chinese state-backed hacker group RedEcho. This was revealed in a webinar on March 9, by the U.S.-based cybersecurity organization Recorded Future. In its report “China-linked Group RedEcho Targets the Indian Power Sector Amid Heightened Border Tensions,” Recorded Future cites geopolitical reasons and heightened border clashes between the two Asian neighbors – India and China – since last May, as the reasons for these attacks. The report does not include any activities post-February 7. For the news story, which CISO MAG published on RedEcho, click here.
— Brian Pereira, Editor-in-Chief, CISO MAG
Recorded Future recently launched a network traffic analysis source which helps it trace the attacks from the targets/victims back to the attackers. It collects threat intelligence from various sources and transforms the information into actionable intelligence, through its platform and security intelligence graph. And it offers six solutions: brand intelligence, SecOps intelligence, threat intelligence, vulnerability intelligence, third-party intelligence, and geopolitical intelligence. Recorded Future disseminates threat intelligence through its portal, mobile application, browser extension, and API for integrations. It also advises governments and institutions alike, on mitigation strategies.
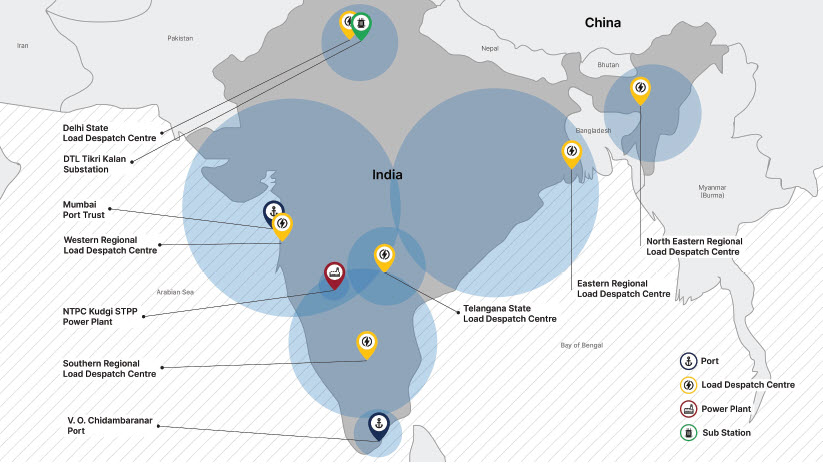
Since early 2020, Recorded Future’s Insikt Group observed a large increase in suspected targeted intrusion activity against Indian organizations from Chinese state-sponsored groups. From mid-2020 onwards, Recorded Future’s midpoint collection revealed a steep rise in the use of infrastructure tracked as AXIOMATICASYMPTOTE, which encompasses ShadowPad command and control (C2) servers, to target a large swathe of India’s power sector. Ten distinct Indian power sector organizations, including four of the five Regional Load Despatch Centres (RLDC) responsible for the operation of the power grid through balancing electricity supply and demand, have been identified as targets in a concerted campaign against India’s critical infrastructure. Other targets identified included two Indian seaports.
“We have been tracking the malicious activities of the RedEcho group since October 2020. And we have observed significant, sustained, high-volume traffic from Indian power sector assets to RedEcho infrastructure. RedEcho has overlapping MO with several Chinese groups, but we chose to name them because at this time, we do not have information to make a definitive connection to a specific existing group. The RedEcho infrastructure is still active, with the last observation on February 28, with comms to NTPC infrastructure,” said Charity Wright, Cyber Threat Intelligence Analyst with Recorded Future’s Insikt Group.
It was observed that RedEcho attacked National Thermal Power Corporation (NTPC) infrastructure. Recorded Future first observed RedEcho’s activity in October 2020. It also informed the Indian Government about the intrusion on October 10, which was two days before the major power outage experienced in the city of Mumbai and its satellite towns and cities.
However, Recorded Future cannot ascertain if the Mumbai power outage on October 12 was due to the RedEcho attacks.
According to a report in India Today, the Maharashtra state load despatch centre was targeted in October 2020.
“We cannot link that particular incident to RedEcho at this time,” said Wright.
Recorded Future again notified the Indian Government about the attacks on infrastructure on February 10 this year, and on February 11, India and China signed an agreement for de-escalation along Pangong Lake near the LAC (line of actual control).
Power companies in other counties have been targeted as well.
“A year ago, Recorded Future revealed an intrusion into a European energy organization (ENTSO-E), by a non-Chinese group. We used a similar methodology based on combining adversary infrastructure detection with network traffic analysis. We discovered a PuppyRAT malware campaign in late 2019. We published those findings on January 23, 2020 and the victim announced the intrusion on March 9, 2020,” added Wright.
Related Story:
Chinese Hacking Group “RedEcho” Targets Indian Power Sector
Key Judgments from Recorded Future
- The targeting of Indian critical infrastructure offers limited economic espionage opportunities; however, we assess they pose significant concerns over potential pre-positioning of network access to support Chinese strategic objectives.
- Pre-positioning on energy assets may support several potential outcomes, including geostrategic signaling during heightened bilateral tensions, supporting influence operations, or as a precursor to kinetic escalation.
- RedEcho has strong infrastructure and victimology overlaps with Chinese groups APT41/Barium and Tonto Team, while ShadowPad is used by at least five distinct Chinese groups.
- The high concentration of IPs resolving to Indian critical infrastructure entities communicating over several months with a distinct subset of AXIOMATICASYMPTOTE servers used by RedEcho indicates a targeted campaign, with little evidence of wider targeting in Recorded Future’s network telemetry.
To view the complete list of IoCs related to the RedEcho threat group, click here.
 Stanley Mierzwa, Director, Center for Cybersecurity at Kean University, U.S., said, “Those organizations recently attacked should consider studying, or if unavailable, employing proper Information Governance strategies to help with the protection of data, as an invaluable asset. This effort will entail going back to the drawing table to study the legal and sector-related regulations, so that they are met, but more importantly so that they are exceeded! This focal action will include a process to employ tasks to help categorize the most critical and important information and data. Ensure to engage appropriate Information Governance policies that will help to enforce security-related information technologies, such as encryption, strict access controls, information rights management, digital shredding capabilities, auditing, and logging.”
Stanley Mierzwa, Director, Center for Cybersecurity at Kean University, U.S., said, “Those organizations recently attacked should consider studying, or if unavailable, employing proper Information Governance strategies to help with the protection of data, as an invaluable asset. This effort will entail going back to the drawing table to study the legal and sector-related regulations, so that they are met, but more importantly so that they are exceeded! This focal action will include a process to employ tasks to help categorize the most critical and important information and data. Ensure to engage appropriate Information Governance policies that will help to enforce security-related information technologies, such as encryption, strict access controls, information rights management, digital shredding capabilities, auditing, and logging.”
Mierzwa lectures at Kean University on Cybersecurity Risk Management, Cyber Policy, Digital Crime and Terrorism, and Foundations in Cybersecurity. He is a regular contributor to CISO MAG. Be sure to read Mierzwa’s article in the April 2021 issue of CISO MAG.
About the Author
Brian Pereira is the Editor-in-Chief of CISO MAG. He has been writing on business technology concepts for the past 26 years.










