
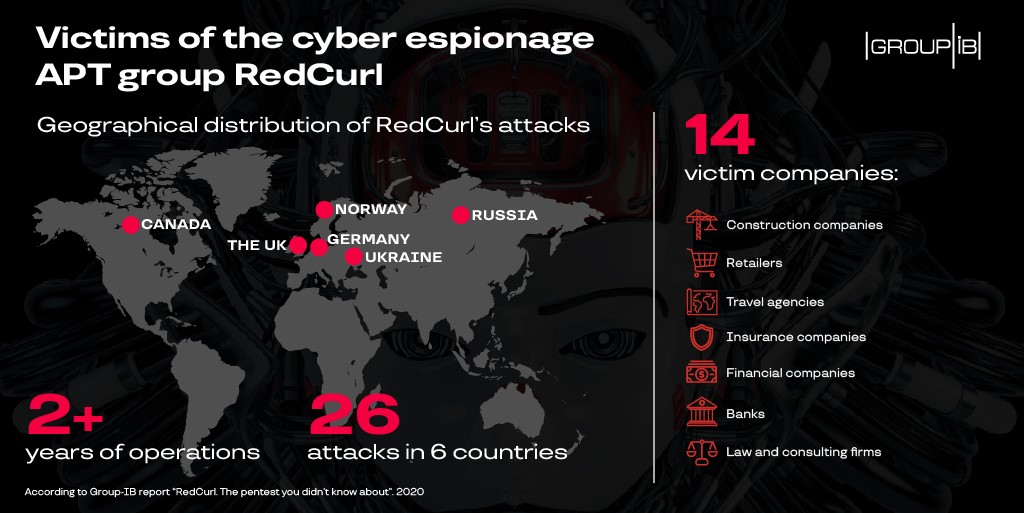
The researchers at Group-IB, a Singapore-based cybersecurity company, have found that a Russian-speaking APT group, RedCurl, has been sniffing through the corporate networks since May 2018 and stealing insider information like employee data and company trade and financial secrets. The RedCurl operators have precisely targeted 26 organizations worldwide and are likely to spread its outreach in the near future.
Key Highlights
- RedCurl is a Russian-speaking APT Group.
- It has conducted 26 targeted attacks on commercial organizations, out of which 14 were successful.
- Its targets are spread across multiple fields including construction, finance, consulting, retail, banking, insurance, law, and travel.
- The targeted companies are located in Russia, Ukraine, the U.K., Germany, Canada, and Norway.
- It uses phishing and spear-phishing campaigns for the spread.
- Its operators use PowerShell script to go undetected against legacy security solutions.
- The attackers used legitimate cloud storage services like Cloudme, koofr.net, pcloud.com, etc. for communicating with the victim’s infrastructure.
The Use of Phishing and Spear-Phishing Tact
Initially, the hacker group carried out extensive research about their targets and drafted a well-written phishing email posing as the target company’s HR staff. They sent emails to multiple employees in the same department, which made them less vigilant. For example, the employees would receive the same email of annual bonuses.
The attackers gave special attention while drafting the spear-phishing email content. The emails had legitimate-looking company addresses and logos and featured the sender address in the company’s domain name.
Delivering Through the Cloud
RedCurl operators also strategically placed the malicious links to its payloads in the emails. They used archives, which directed their potential victims to legitimate cloud storage software like Cloudme, koofr.net, pcloud.com, etc., making them believe that they were opening a legitimate file containing information about the annual bonus breakdown. On clicking the link, it would download a Trojan downloader on the victim’s network called RedCurl.Dropper (hence the name). Any person trying to open this file would initiate the malware installation, which in turn would drop other payloads to search the network and exfiltrate data from all types of files and folders back to the cloud.
What needs to be noticed is how the hackers used cloud technology for infection and exfiltration instead of the traditional CnC/2C (command and control) server. This shows that the threat vectors are evolving and cybercriminals are getting smarter by the day. What will be interesting is to see how the defenders evolve.










