The researchers from SophosLabs revealed that fleeceware app developers are operating on Apple’s App Store for iPhones and iPads. They claimed that more than 3.5 million iPhone users have been impacted by the malicious fleeceware apps on their devices....
Researchers at Group-IB, a Singapore-based cybersecurity company, have found out that amid the rising concerns of restructuring and reuse of previously known malware families, phishing kits have become a popular choice for spreading them. Phishing kits have now gained...
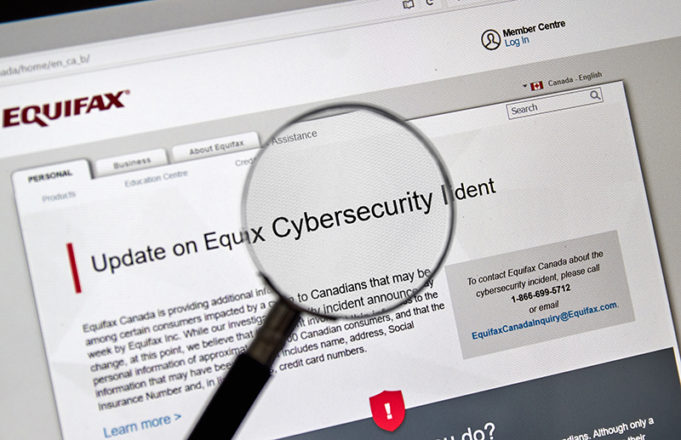
Atlanta-based consumer credit reporting agency Equifax has agreed to pay the State of Indiana $19.5 million to settle a class-action lawsuit, brought forward by the State’s Attorney General Curtis Hill. The lawsuit concerns the 2017 data breach that leaked...
Amid the COVID-19 pandemic, more employees in Australia are opting for self-isolation and choosing to work from home. But there are concerns about these users falling victims to phishing attacks. To protect users, the Australian Cyber Security Centre (ACSC)...
Connected cars manufactured by Ford and Volkswagen have major security flaws which could put owners’ privacy and safety at risk, a new research found. An investigation from consumer group Which? exposed vulnerabilities in connected technology like media and computer...
Apple was the most frequently used brand in phishing attacks during the first quarter of 2020, according to Check Point’s research. The research report “Brand Phishing Report” revealed that nearly 10% of all brand phishing attempts in 2020 so...
You may have a very mature security program for your organization with comprehensive technical and administrative security controls. You have stopped a variety of dangerous events in the past 12 months and you can see things are going well...
Pakistan-based cybersecurity company, Rewterz Threat Intelligence, discovered a sale advertisement of 115 million Pakistani mobile users’ data being put up on the dark web by an undisclosed hacker.
Researchers at Rewterz said that the threat actors are monetarily motivated as...
With organizations working remotely, cybersecurity works as a core technology to keep companies secure. The Indian cybersecurity market will witness an increase in the demand for cybersecurity and privacy post the COVID-19 pandemic, according to IANS.
Experts opined that, once...
Introduction
Whether for ensuring business continuity or enhancing workforce retention and productivity, more organizations are embracing mobility, work-at-home and flex-time for their employees. To achieve business goals with a mobile and remote workforce, having a robust and reliable access security...