
We, cybersecurity professionals, have been hiding behind lies for a few years now.
“Cybersecurity is a new industry. There is not enough data to measure maturity”
“Maturity models work where there are well-defined processes to follow. Like software development. Not cybersecurity. We live a new problem every day.”
All hogwash. Or as Roald Dahl’s BFG would put it – ‘Redunculus.’
It’s about time CISOs stop making excuses – and started taking concrete steps to measure their cybersecurity maturity.
By Chaitanya Kunthe, Co-founder and Chief Operating Officer at Risk Quotient
What exactly is a maturity model?
Every CISO has faced existential questions like these:
Is our cybersecurity improving? What do we do to improve further?
Are we better off today than we were last year? How do we know that?
Capability and maturity models answer these questions. For more details read this paper.
A maturity model allows an organization to assess its practices against a clear set of benchmarks. Evaluating against these benchmarks provides an organization with a clear understanding of where they currently are and provides a roadmap to improve its maturity.
There are two types of maturity models – ‘progression’ models and ‘capability’ models. Combining the two creates a third type – hybrid.
Progression Models: Logs enabled and reviewed on servers → Centralized Logging and Alerting → SIEM implemented. Here, the core requirement is the monitoring of logs. What changes is the way monitoring is done. Automated ways of doing things move you up the ranking. You progress from a manual way of doing things to an automated way of doing things.
Capability Maturity Models: Ad hoc event reporting → Defined events and incidents → Risk-based event and incident monitoring and reporting. Here, the core requirement is reporting and managing incidents. The focus is on process maturity. You progress from an ‘ad-hoc’ process to a managed and measured process.
Both of these models have certain inherent problems. The progression model might lead you down a very sticky ‘tool’ driven path where the solution to every problem would be to implement a new tool. The capability maturity model can take you down a very theoretical path of ‘measured,’ ‘monitored,’ ‘managed’ and creating MBs of documents and processes. The hybrid model blends the best part of both these approaches.
Hybrid Models: Incidents reported in an ad-hoc manner → Criteria for reporting defined. Central Logging enabled → Pattern analysis to detect incidents automatically, risk-based incident scoring. A hybrid model uses a mix of both progression and capability maturity models.
Why go for a cybersecurity maturity model?
Measuring cybersecurity is like trying to find that irritating noise in your car. You know it is there. You can hear it. You just don’t know where it is. You know you have to measure cybersecurity effectiveness. You just don’t know what to measure and how.
Is your cybersecurity effective? There are two ways to find out – the simple way and the hard way.
The simple way is to go through a third-party audit and certification. Rely on global standards like ISO 27001, PCI-DSS, NIST-CSF. Hire auditors. Trust that the auditors you have hired understand your environment and assess you. In a fair and accurate manner that it improves your cybersecurity.
The hard way is to define your own metrics and measurement based on risks. This is way more effective, but a self-assessment is not what your customers and regulators will accept easily.
In both these methods, you do not have a clear path to improvement. Cybersecurity maturity frameworks give you this path (Not to mention it helps getting budgets approvals).
Which one, then?
If you’ve read so far, you are probably wondering which framework to go for. Veterans in information security would recollect a maturity model called the SSE-CMM. Systems Security Engineering – Capability & Maturity Model. The SSE-CMM website no longer exists, but you can see what the standard was like by visiting this URL: SSE-CMM Home Page.
This was way back in 2003. Then for more than a decade, no one spoke of cybersecurity maturity. Today, there are two good cybersecurity maturity frameworks that you can choose from.
The first one is the Cybersecurity Maturity Model Certification (CMMC) from the U.S. Department of Defense. This model is in the news as it is now mandatory for defense contractors in the U.S. to certify themselves on the CMMC. The CMMC is a hybrid model. There are five maturity levels in the CMMC.
- Level 1 – Performed
- Level 2 – Documented
- Level 3 – Managed
- Level 4 – Reviewed
- Level 5 – Optimizing
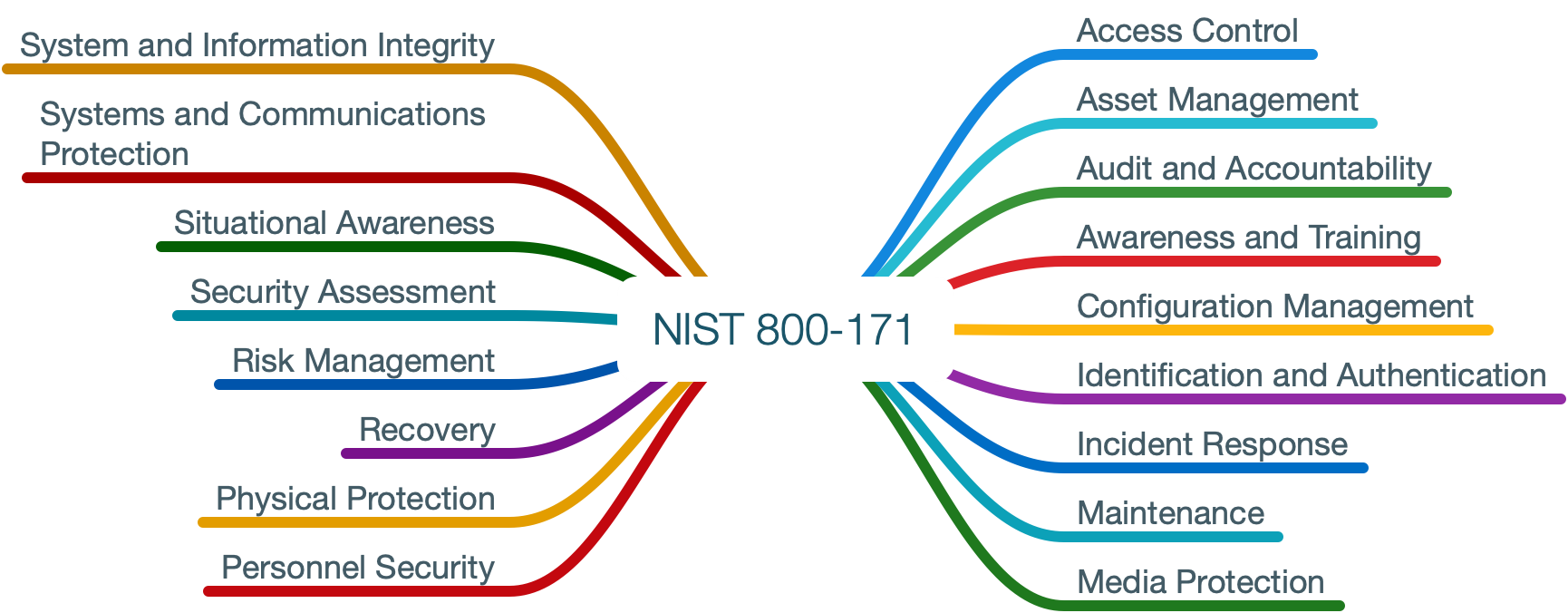
The maturity levels combine with the 17 domains of NIST 800-171 to make the model.
The second framework comes from the U.S. Department of Energy. It is the Cybersecurity Capability Maturity Model or the C2M2. C2M2 was built for critical infrastructure in the energy sector. It has now expanded to include models specific to the electricity sub-sector and the oil and natural gas sub-sector. Further sector specific models are planned too.
This framework has four maturity indicator levels (MIL)
- MIL0 – No practices
- MIL1 – Ad-Hoc practices
- MIL2 – Initial level of institutionalization of practices
- MIL3 – Further institutionalized and managed
C2M2 model has 10 domains. You can be on different levels in different domains.

Another interesting maturity model to consider is the FISMA metrics. Again, a U.S. government initiative. It focuses on maturity around five function areas of Identify, Protect, Detect, Respond, and Recover, though it might not directly map to NIST-CSF.
How should you go about it?
Go through the domains of both the standards and choose the framework most appropriate to you. Perform a self-assessment – know where you stand. Be ruthlessly honest about it. If you have a trusted and mature third party who can do the assessment for you, bring them in.
The self-assessment is the beginning. What you do after that is more important. Create a dashboard of the domains and your maturity at each domain and control. Define a ‘to-be’ maturity goal for your organization. Get the relevant stakeholders to agree on this goal. This dashboard becomes your maturity tracker. Implement practices and controls as required and regularly assess yourself for where you stand. Involve the security leadership, else it will reduce to a compliance show that you put up.
A word of warning: Do not go about this exercise as a simple compliance exercise – else you will be subject to the same problems as any other compliances that you maintain. For more information, read:
Cybersecurity Maturity Model Certification: An Idea Whose Time Has Not Come And Never May
If you choose to go about this exercise, then here are some tips to make it effective:
- Involve the security leadership, else it will reduce to a compliance show that you put up.
- Focus on improvement and measuring that improvement (through your dashboard). Not only on moving up maturity levels.
- You do not have to be at the highest maturity level. Choose your goals wisely based on your risks.
Finally, remember, any exercise of cybersecurity maturity and measurement can be effective or ineffective based on the intent behind the exercise. Choose wisely.
About the author
 Chaitanya Kunthe is a seasoned cybersecurity mentor who believes in simplifying things. He is the Co-founder and Chief Operating Officer at Risk Quotient, where he mentors the team to provide innovative and practical cybersecurity advice.
Chaitanya Kunthe is a seasoned cybersecurity mentor who believes in simplifying things. He is the Co-founder and Chief Operating Officer at Risk Quotient, where he mentors the team to provide innovative and practical cybersecurity advice.
Disclaimer
Views expressed in this article are personal. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.










