
CISO MAG Desk: John McAfee recently declared that his twitter account was hacked and used to endorse some minor-league cryptocurrencies. Although, he claimed to have enabled the two-factor authentication, his mobile phone was jeopardized leading to the cyber attack on his social media account.
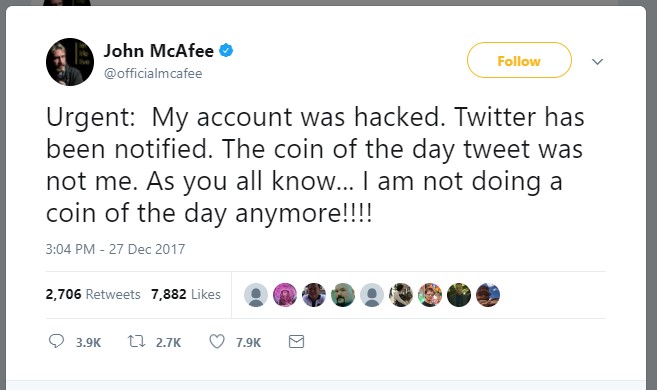
The former presidential candidate said that he got the first indication of his phone being hacked when he turned it on, to see a dubious error message on the screen. In an interview to BBC John mentioned, “I knew at that point that my phone had been compromised. I was on a boat at the time and could not go to my carrier (AT&T) to have the issue corrected. All that the hacker did was compromise my Twitter account. It could have been worse.” Considering that only the Twitter account of the former owner of one of the world’s first anti-virus companies was attacked, led to a lot of witticism from different corners.
While cybersecurity experts are assessing the perils of AI empowered cyber breaches, it is indeed worrisome that the frequency of break-ins have increased and the targets can be any avenues, irrespective of their influence, importance or seriousness. Although John McAfee’s account hacking is debatable, but the rapid surge in cyber attacks has led to reconsidering the present cybersecurity guidelines and methodologies.










