
Security experts from IT giant HP announced that it has discovered multiple security vulnerabilities in certain versions of its HP Device Manager, a software that allows system administrators to manage their HP Thin Client devices. In a security advisory, HP stated the vulnerabilities could allow malicious actors to remotely gain unauthorized access to resources and also SYSTEM privileges. The flaws could also expose the Device Manager to dictionary attacks due to weak cipher implementation. In dictionary attacks, hackers try to obtain illicit access to a system by using a large set of words to generate potential passwords.
The issue came to light after security researcher Nick Bloor reported about the vulnerabilities. Bloor stated that an HP developer put a backdoor database user account in HP Device Manager, which leads to unauthenticated remote command execution as SYSTEM.
“Do you or your clients use HP thin clients and manage them with HP Device Manager? I strongly advise you, firstly, to log on to all servers running HP Device Manager and set a strong password for the ‘dm_postgres’ user of the ‘hpdmdb’ Postgres database on TCP port 40006,” Bloor added.
The vulnerabilities and affected versions include:
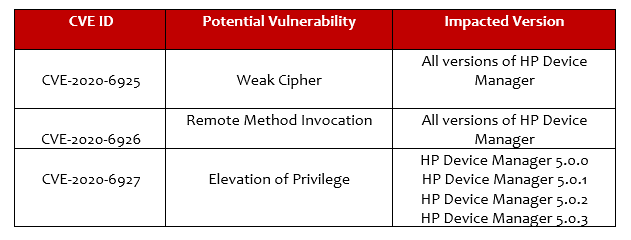
However, HP clarified that the CVE-2020-6925 vulnerability does not impact the users who are using Active Directory authenticated accounts. It also added that the CVE-2020-6927 flaw does not impact customers who are using an external database and have not installed the integrated Postgres service.
HP is stated that it will release security patches for all the vulnerabilities. Meanwhile, the company recommended certain security steps to partially mitigate the issues by:
- Limiting incoming access to Device Manager ports 1099 and 40002 to trusted IPs or localhost only.
- Removing the dm_postgres account from the Postgres database.
- Updating the dm_postgres account password within HP Device Manager Configuration Manager.
- Creating an inbound rule within Windows Firewall configuration to configure the PostgreSQL listening port (40006) for localhost access only.
“HP is broadly distributing this security bulletin to bring to the attention of users of the affected HP products the important security information contained in this Bulletin. HP recommends that all users determine the applicability of this information to their individual situations and take appropriate action,” HP added.










