
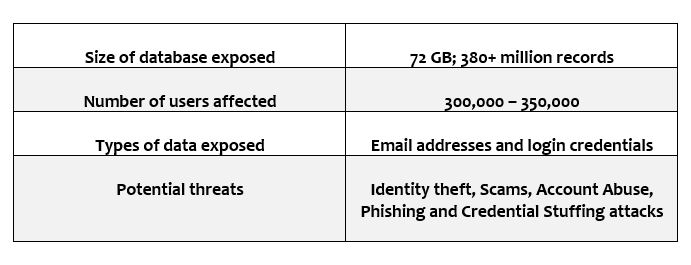
Security experts from vpnMentor uncovered a potential credential stuffing attack exploiting the personal data of Spotify users. The researchers found an unencrypted Elasticsearch database containing over 380 million records holding login credentials and other personal details of the music streaming service users. In credential stuffing attacks, cybercriminals take advantage of weak and reused passwords of consumers with the hope of eventually guessing correctly.
The threat actors behind the exposed database are unknown, however, they abused stolen login credentials to compromise Spotify accounts. “Working with Spotify, we confirmed that the database belonged to a group or individual using it to defraud Spotify and its users. We also helped the company isolate the issue and ensure its customers were safe from attack,” vpnMentor said.
Threat Summary:
Origin of the Database
vpnMentor’s researchers stated that the exposed database belonged to a third-party service provider that was using it to save Spotify users’ login details. It is found that attackers illicitly obtained user credentials from data breaches and from other sources.
“This is a common tactic used by cybercriminals to access private accounts on popular platforms like Spotify, and something the company — like most online businesses — has dealt with in the past, given the pervasive use of weak passwords by so many consumers online. Companies cannot prevent this from occurring since they do not control the passwords that consumers use (and re-use) online. But they can play a role by helping users regain control of their accounts and promoting safer password practices by users, which Spotify did in this case,” vpnMentor added.
Spotify notified the affected users to reset their passwords as a security measure.










