
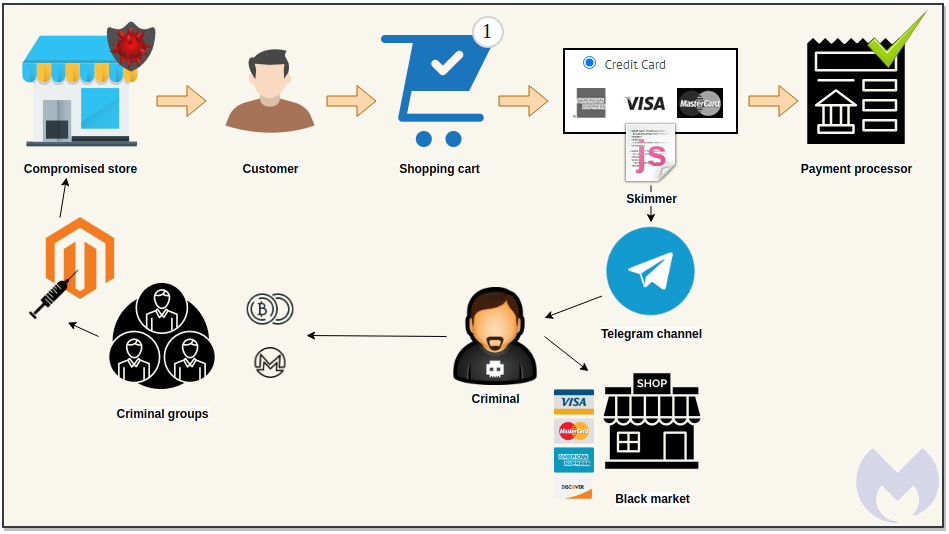
Cybercriminals constantly adopt new attack techniques to implement their malicious activities. Recently, Magecart attackers implemented a new web skimming technique by leveraging the popular messaging app Telegram to pilfer card data.
Telegram-Based Skimming Attack
According to Malwarebytes, hackers exploited the Telegram app to send stolen payment details from compromised websites. They used the messaging platform to exfiltrate sensitive data by deploying skimmer codes and traditional Trojans.
“The fraudulent data exchange is conducted via Telegram’s API, which posts payment details into a chat channel. That data was previously encrypted to make identification more difficult. For threat actors, this data exfiltration mechanism is efficient and does not require them to keep up infrastructure that could be taken down or blocked by defenders. They can even receive a notification in real time for each new victim, helping them quickly monetize the stolen cards in underground markets,” Malwarebytes said.
According to the security researcher AffableKraut — who is the first to disclose the incident in a Twitter thread — the skimmer code checks for web debuggers to evade security detection and looks for sensitive data fields like billing, payment details, credit card number, expiration, and CVV.
Injecting e-skimmers or malicious JavaScript on e-commerce sites to pilfer payment card details is a common technique used by Magecart operators. But this time, they used a new method to exfiltrate data through a message sent to a Telegram channel using an encoded bot ID in the skimmer code.
“Defending against this variant of a skimming attack is a little more tricky since it relies on a legitimate communication service. One could obviously block all connections to Telegram at the network level, but attackers could easily switch to another provider or platform (as they have done before) and still get away with it,” Malwarebytes added.










