
Cybersecurity experts from Check Point found threat actors dropping new malware via nine malicious Android apps on the Google Play store. Dubbed as Clast82, the new malware allows an attacker to illicitly obtain victims’ financial information by taking full control of their mobile devices. The search engine giant has removed the apps from the Play store after being notified by Check Point researchers.
Clast82 Malware Dropper
The researchers stated that Clast82 malware can avoid Google Play Protect detection and change the payload dropped from a non-malicious payload to the AlienBot Banker and MRAT. Upon taking control of a device, the attacker can perform certain functions like installing a new application on the device or even control it with TeamViewer.
“The AlienBot malware family is a Malware-as-a-Service (MaaS) for Android devices that allows a remote attacker to inject malicious code into legitimate financial applications,” Check Point said.
The Nine Malicious Apps
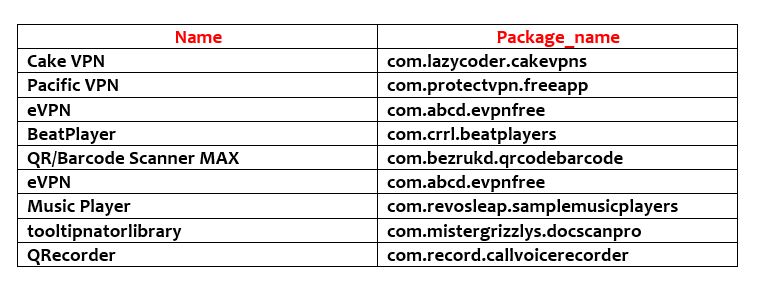
“The malware’s ability to remain undetected demonstrates the importance of why a mobile security solution is needed. It is not enough to just scan the app during the evaluation period, as a malicious actor can, and will, change the application’s behavior using 3rd party tools. As the payload dropped by Clast82 does not originate from Google Play, the scanning of applications before submission to review would not prevent the installation of the malicious payload. A solution that monitors the device itself, constantly scanning network connections and behaviors by application would be able to detect such behavior,” Check Point added.










