
By Joshua Blackborne
Cyberattacks have become a part of the reality of doing business in today’s digital landscape. Almost every company relies on computers, digital tools, and the internet these days, and this leaves us all exposed to cyberthreats.
Hackers and scammers today have easier access to increasingly sophisticated methods that allow them to exploit vulnerable devices and users. Companies whose digital infrastructures fall victim to these attempts are exposed to a variety of attacks such as data breaches, ransomware, and fraud. According to its latest threat report, McAfee Labs saw an average of 504 new threats per minute in Q1 of 2019 alone.
Experts expect attacks to persist and even grow in the coming years. As such, security needs to be part of every company’s business strategy. Fortunately, the cybersecurity community has been putting up a good fight against attacks, developing tools that help mitigate the risks posed by hackers and scammers.
Here are five security solutions that you can use to protect your company from vulnerabilities, attacks, and scams as we all get set for 2020.
Secure Your IoT With FirstPoint’s Virtual Mobile Networks
Companies are now aggressively adopting mobile and Internet-of-Things (IoT) devices. Many of these devices, however, rely on cellular connectivity.
The problem is that cellular networks can be exploited. Hackers can now use fake cell towers, location tracking, SMS phishing, and SSL loopholes to intercept data or even gain access to devices that rely on cellular connectivity. Once they take control of these connections, the hackers can readily eavesdrop on all the data being transmitted over the network and even install malware into connected devices, often without anyone even knowing.
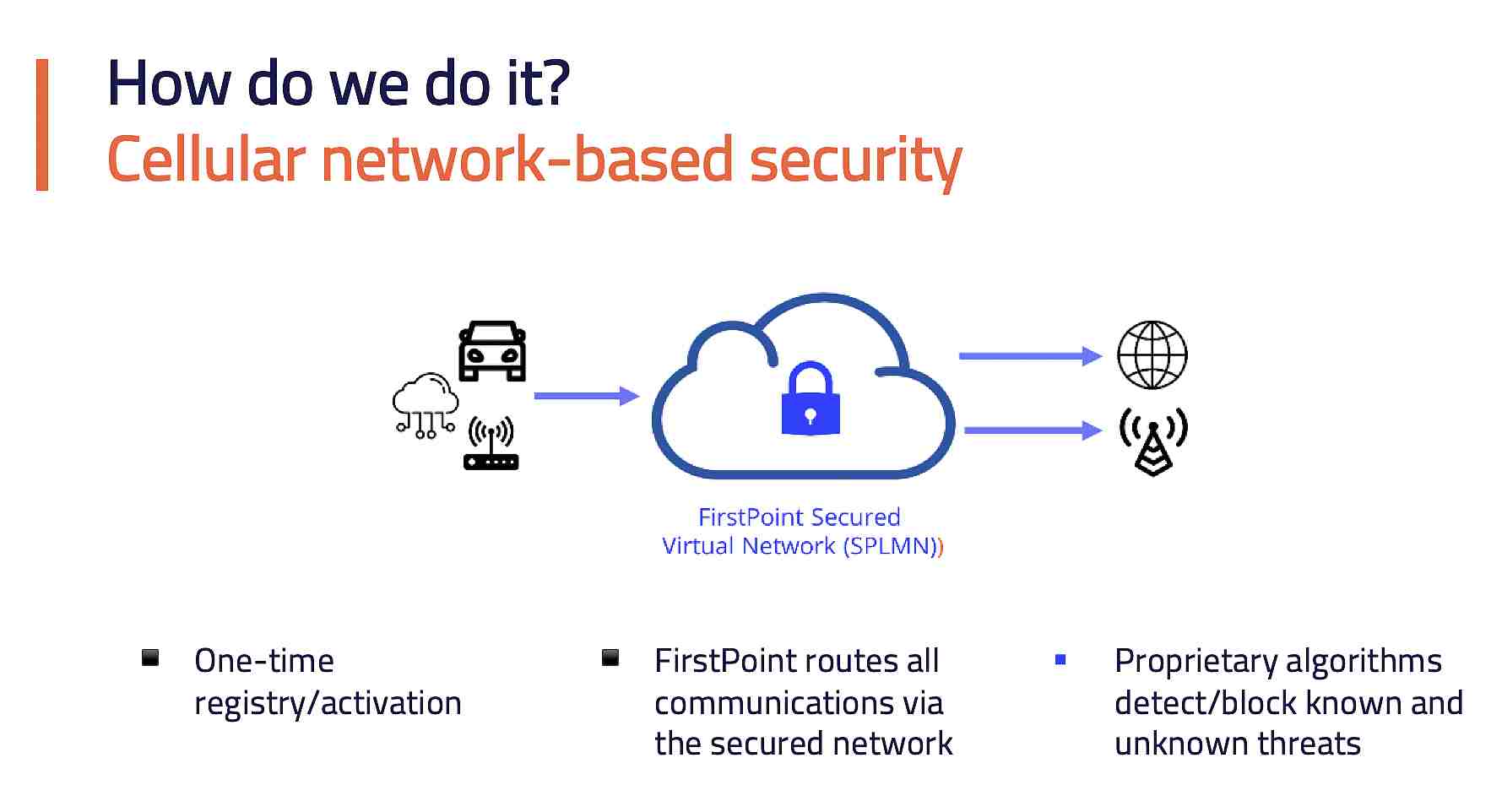
Employed by telecoms who are looking to cater to key clients who require a high-fidelity security solution, FirstPoint has created a solution designed to specifically secure cellular connections at the network level. Once integrated, FirstPoint essentially routes all information between a user and the cellular network through a secure virtual network. Using advanced algorithms, all traffic that passes through this secure network is scanned for threats.
Should any malicious traffic or processes be detected, FirstPoint can effectively screen and prevent these from executing.
Get All Hands on Deck With Cymulate’s Attack Drills
Another major challenge for businesses is knowing whether their chosen cybersecurity tools actually work. Typically, testing defenses involves performing penetration tests that probe networks for vulnerabilities. IT teams can also form “read teams” that take on the role of hackers and employ similar attack methods to test their security.
Unfortunately, both approaches require high levels of technical skills to pull off. Contracting third parties to perform these can also be expensive.
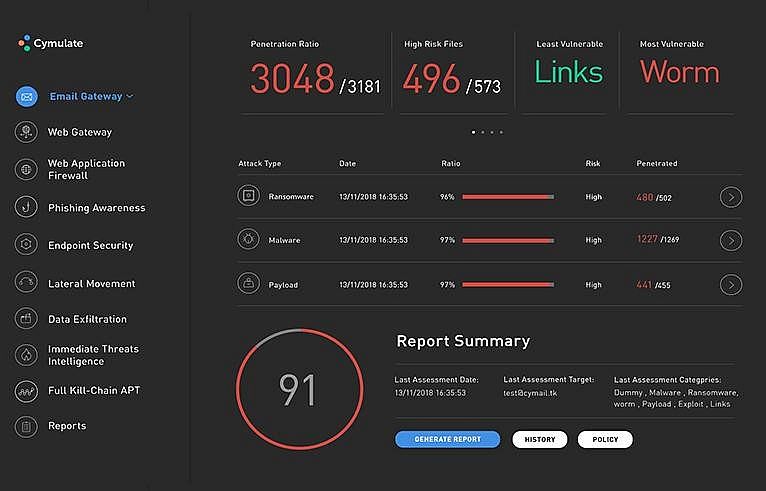
As an alternative, organizations can use Cymulate’s breach and attack simulation (BAS) platform to test their defenses. Cymulate simulates various attacks across vectors. It can test the effectiveness of endpoint security solutions such as anti-viruses and anti-malware by deploying payloads on target machines. It can also test the security of email, web applications, and servers to ensure that all components comprising a company’s infrastructure are protected.
After testing, the platform generates a comprehensive report and a score to help security teams identify weak and vulnerable areas so that they can commit to corrective actions. Since solutions and threats evolve, Cymulate can automatically test periodically to ensure that everything works as it should.
Reward Social Reengineering with Hoxhunt’s Phishing Drills
The human element continues to be the weak link in cybersecurity defense. An Egress study showed that human error was the main cause of 60 percent of personal data breaches reported between January 1 and June 20 of 2019.
Human fallibility is why hackers continue to perform social engineering attacks as a means to gain access to enterprise systems. Phishing, or the use of fraudulent messages to trick users into giving up information or installing malware into their devices, remains a popular attack method among hackers.
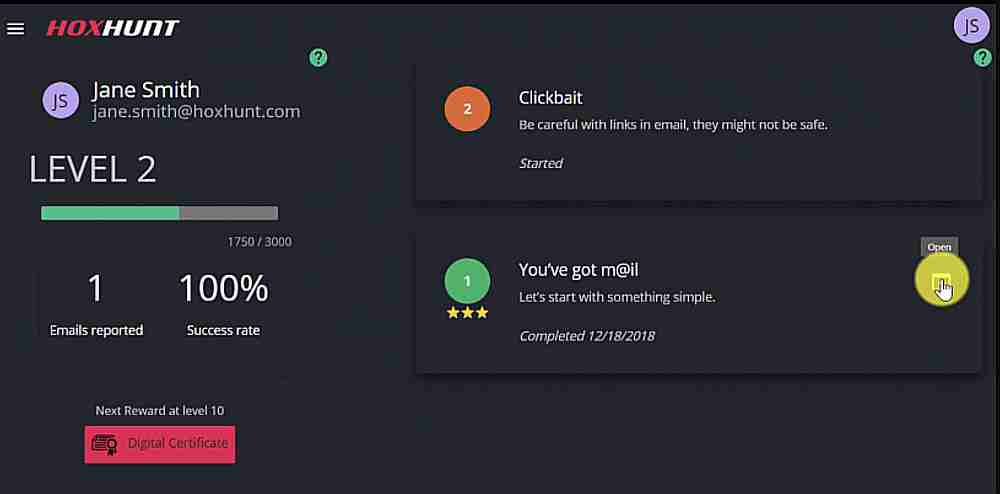
Hoxhunt allows enterprises to enhance security by focusing on improving the human element. It provides automated phishing training for all members of the organization in a sustained manner, and while in a real working environment.
Hoxhunt generates ML-powered personalized simulated phishing emails directed to specific users and provides feedback on how well users react to these simulated attacks. Through proper ongoing, in-context training and a gamified experience, teams can distinguish these fraudulent messages and report the emails. That’s why Hoxhunt says its customers quickly find failure rates diving to under 2 percent.
Seamlessly Prevent Payment Fraud with Signifyd’s Authentication Tool
Businesses operating in the e-commerce space are always exposed to the threat of online fraud. Stolen credit card information can be purchased on the cheap from the dark web. Scammers and fraudsters often take advantage of this by using these stolen accounts to purchase goods online.
Unfortunately for e-commerce merchants, card companies generally rule in favor of customers when these fraudulent charges are contested. When disputes and chargebacks happen, businesses have no choice but to refund the transaction and bear the brunt of expenses such as the cost of goods and shipping.
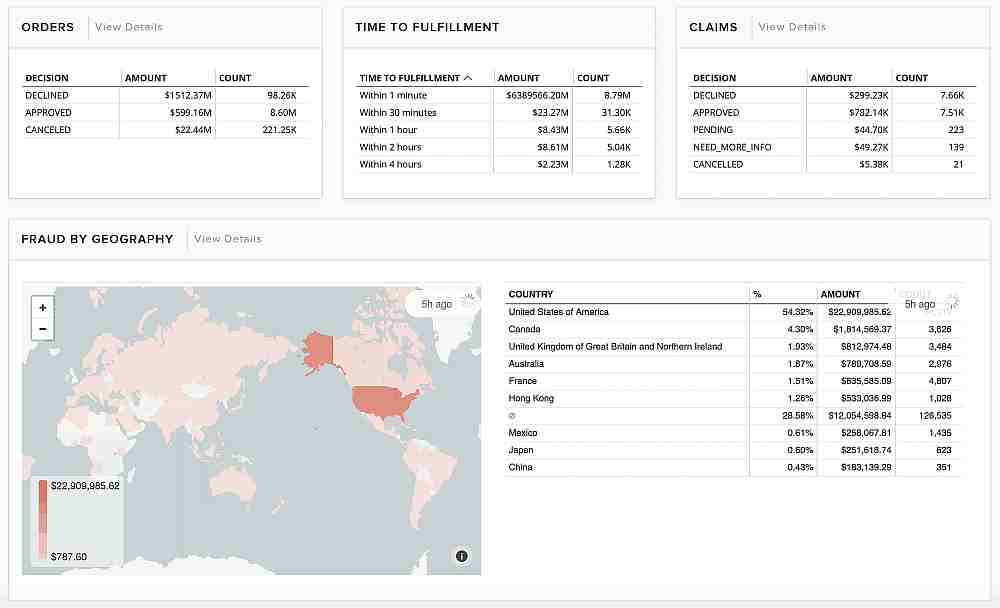
As such, it’s important for businesses to have fraud prevention and protection. Signifyd offers a comprehensive service that combines big data, machine learning, and manual reviews to check the authenticity of transactions.
Integrating with popular shopping carts like Shopify, BigCommerce, and Magento, this platform also improves customer retention by minimizing instances of falsely declined payment attempts. Online shoppers readily abandon merchants that erroneously deny their legitimate transactions, so advanced fraud prevention allows companies to minimize revenue leakage from both losses and churn.
Reveal and Manage SaaS Access Permissions with Torii
The problem of shadow IT, or the use of unauthorized devices and applications, has been a constant concern of IT teams over the years. The phenomenon has become even more alarming thanks to the rise of cloud-based services and software-as-a-service (SaaS) as a distribution method for applications since it allows just about anyone to subscribe to apps and services on a DIY basis.
Shadow IT can create some major problems for organizations. Companies may be spending unnecessarily on redundant apps. But if people use insufficiently secure apps, or if they grant SaaS tools permission to access network resources like contact databases or email messages, new vulnerabilities are released into the infrastructure, without IT even knowing it. As a result, data may get lost, destroyed or intercepted, and data privacy regulations can be unwittingly violated.
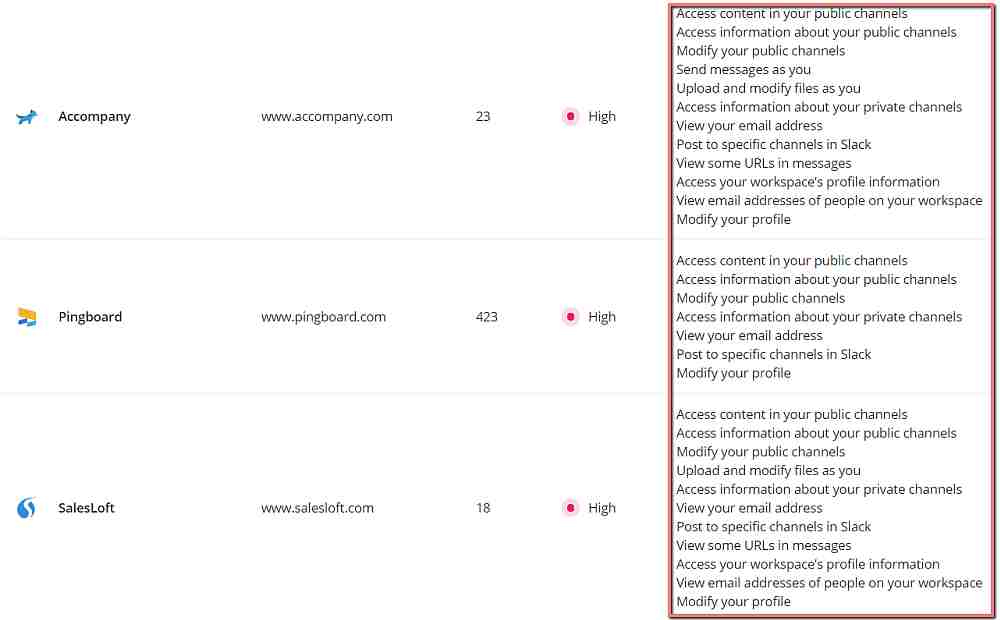
A leading SaaS management platform, Torii helps minimize the dangers of shadow IT by enhancing visibility and reducing latency. It can automatically identify and track all instances of SaaS use within the network. What’s more, Torii’s database displays the risk levels and access permissions that each SaaS product generally demands. This allows administrators to create an accurate, real-time inventory of all SaaS accounts and terminate subscriptions to insecure and non-compliant apps.
Torii also supports automated alerts, as well as custom onboarding and offboarding features that allow IT teams to manage and delegate access to all SaaS accounts via automated workflows.
Strategy is the Key to the Stack
Hackers and scammers are only bound to increase their malicious ways, especially now that they can so easily monetize the data that they steal from companies. Surely, you wouldn’t want your company to be part of the growing number of organizations that fall victim to cyberattacks. As such, it is crucial for you to have a comprehensive cybersecurity strategy that fits your specific context. Knowing where your company is vulnerable and investing the proper tools to strengthen your defenses will be crucial in preventing attacks.
CISO MAG did not evaluate the advertised/mentioned product, service, or company, nor does it endorse any of the claims made by the advertisement/writer. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.










