
A report from IT security solutions provider, Kaspersky, suggests that industrial control systems (ICS) sectors globally have seen a gradual decline in the number of cyberattacks targeted towards them. However, experts observed that the limited number of attacks have now become more complex, targeted, and exclusive in nature. Let’s have a look at the key highlights of the report.
Key Highlights
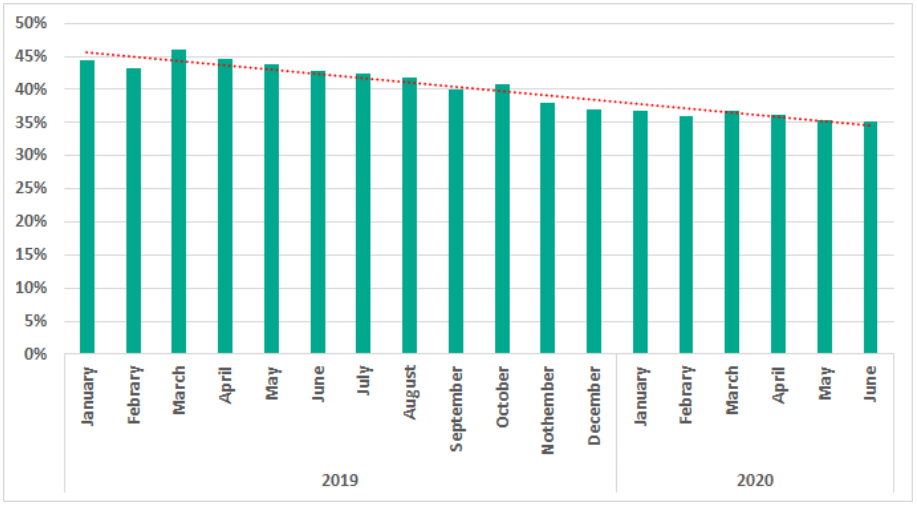
- In H1 2020, the percentage of malicious attempts blocked on ICS computers has decreased by 6.6% and has come down to 32.6% as compared to H2 2019.
- The number was highest in Algeria (58.1%), and lowest in Switzerland (12.7%).
- Despite the overall percentages of attacked computers seeing a downward trend, researchers found growth in the Oil & Gas sector by 1.6 p.p. (percentage points) to 37.8% and by 1.9 p.p. to 39.9 % for computers used in building automation systems.
- Cyberattacks on ICS are seeing increased volumes of backdoors, spyware, Win32 exploits and malware families specifically built on the .Net platform.
- Region wise, Asia and Africa ranked least secured based on the percentage of ICS computers attacked, whereas, southern and eastern regions of Europe were the least secured in the Transatlantic region.
Cyberattacks on ICS Sector
According to the research, 37.8% of computers associated with the ICS sectors suffered a cyberattack in the H1 of 2020. This increased the tally by a mere 2% in comparison to H2 2019. However, this increase is purely associated with the growing number of cyberattacks on ICS sectors of oil and gas along with systems in the building automation space, which again saw a 2% increase and a total of 39.9% of threats in the first half.
Researchers are concerned with the growing variety of new variants of standalone malware being used in these cyberattacks. They have particularly seen an uptrend of different computer worms written in script languages such as Python and PowerShell, for disrupting ICS operations. The biggest spike in these detections came between the end of March and mid-June 2020.
The report said, “Building-automation systems often belong to contractor organizations, and even when these systems have access to the client’s corporate network, they are not always controlled by the corporate information security team. Given that the decrease in mass attacks is offset by an increase in the number and complexity of targeted attacks, where we see active utilization of various lateral movement tools, building automation systems might turn out to be even less secure than corporate systems within the same network.”
A Pinch of Salt
Although the decline in numbers is encouraging, there is a certain uptick in the complexity and exclusivity of the cyberattacks targeted across various ICS verticals. Overall, ransomware contributed towards only 0.63% of the total cyberattacks on the ICS computers. However, with increased complexity like the one observed in EKANS ransomware attack on several ICS systems in the manufacturing sector, is more disruptive than ever.
Apart from this, Kaspersky researchers also noted malicious activities of several APT groups that are actively targeting the ICS and SCADA systems. The impact of COVID-19 has exposed the threat landscape to remote ICS connectivity. Between February and May 2020, there was a clear growth in the percentage of ICS computers on which attempts to crack RDP passwords through brute force attacks were detected.
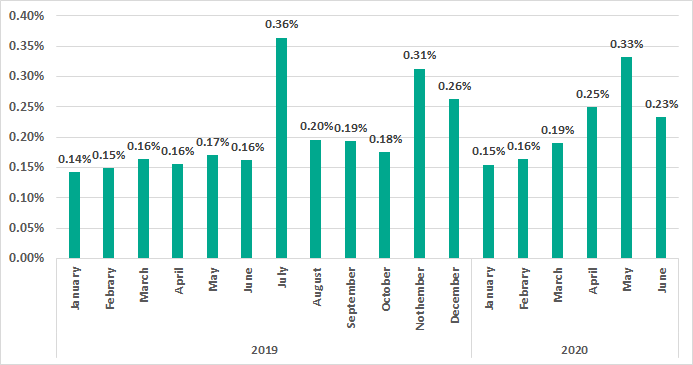
The global outbreak of the pandemic has led to a shift in the threat landscape, and it is a wake-up call for corporates and CISOs to identify, monitor, and protect data in use, data in motion, and data at rest.










