
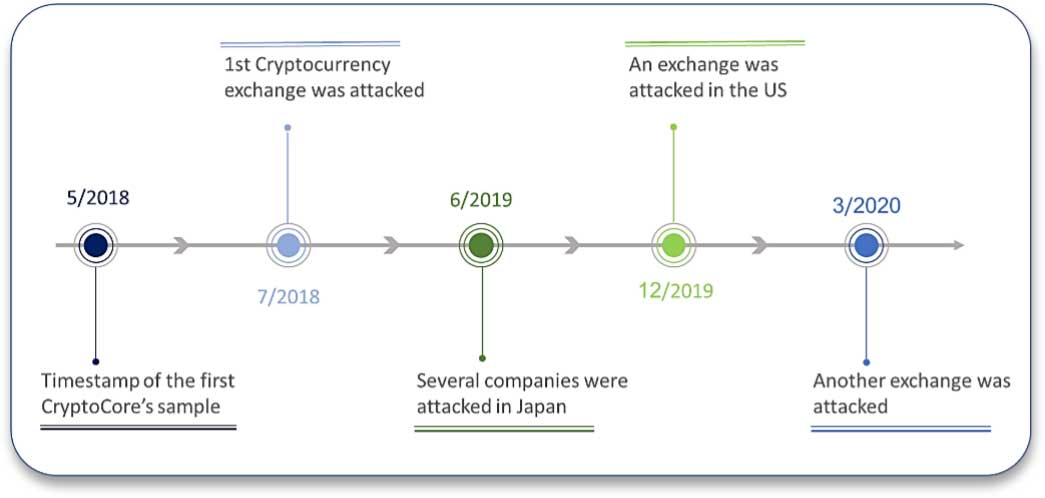
A new report from cybersecurity firm ClearSky revealed that a hacking group “CryptoCore” is targeting cryptocurrency exchanges via spear-phishing campaigns. CryptoCore, also known as Dangerous Password and Leery Turtle, stole cryptocurrency worth $200 million in two years. It is found that the hacking group was targeting companies in the U.S. and Japan since 2018.
“We have been tracking CryptoCore group campaigns for almost two years, with no conclusive understanding of the operators’ origin; however, we assess with medium level of certainty that the threat actor has links to the East European region, Ukraine, Russia or Romania in particular. The key goal of CryptoCore’s heists is to gain access to cryptocurrency exchanges’ wallets, be it general corporate wallets or wallets belonging to the exchange’s employees. For this kind of operation, the group begins with an extensive reconnaissance phase against the company, its executives, officers and IT personnel,” the ClearSky reported.
Spear-Phishing Attacks
ClearSky stated that CryptoCore initiates a reconnaissance phase to identify the email accounts of the cryptocurrency exchange’s employees and security executives before conducting a spear phishing attack. These attacks are performed by using fake domains impersonating affiliated organizations, sending emails that impersonate employees, and spreading malicious links and documents via emails.
“After gaining initial foothold, the group’s primary objective is obtaining access to the victim’s password manager account. This is where the keys of crypto-wallets and other valuable assets – which will come handy in lateral movement stages are stored. The group will remain undetected and maintain persistence until the multi-factor authentication of the exchange wallets will be removed, and then act immediately and responsively,” ClearSky added.
Other Notable Findings on CryptoCore Group include:
- CryptoCore group maintains the same general course of action regarding the infection and post-exploitation stages. While the bait document type, the services the phishing sites mimic, the exact tooling and others may vary, an overarching strategy remains the same.
- The group also appears to steadily use the same titles for its bait documents and even some payloads.
- The group often uses Google Drive as the storage for its files, specifically the baits. Sometimes, the phishing emails contain links claiming to be from Drive, while directing to a copycat site, and sometimes it uses the actual Drive service. Again, Drive is not the only service they use, it is just common.
- We have seen the attackers hide LNK shortcuts behind icons and titles of other file types, mostly text files. Sometimes it could be a password file needed to open the main document, sometimes it could be the main document that is a shortcut, but LNK files are a staple for this group. These files are used to connect to the command and control (C2) server and download next-stage files.
- The group’s infrastructure is continuously and rapidly changing. While in some cases we have seen the same infrastructures being constantly reused, perhaps against multiple victims, the group is generally quick to register and employ new domains and links.










