
By Derek Manky, Chief of Security Insights and Global Threat Alliances, Fortinet
Cybercriminals continue to refine existing malware to evade detection and deliver increasingly sophisticated and malicious payloads. They’re increasingly using banking trojans to drop other payloads and additional banking malware on infected systems to maximize their opportunities for financial gain.
Emotet is an example of this type of iterative process. It is a popular and successful banking trojan primarily spread through spam emails. During its lifecycle, it underwent a few iterations. Emotet had been relatively quiet for months, but Fortinet’s Q3 2019 Threat Landscape Report revealed a sudden surge in spamming activity related to the banking malware.
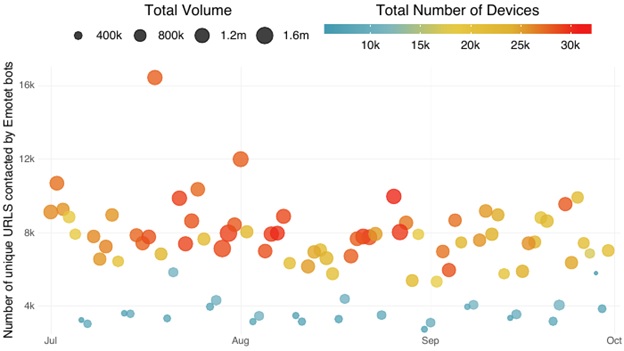
Why this sudden upsurge in activity?
Malicious actors have been using Emotet in a spear-phishing campaign to distribute TrickBot, a dangerous piece of malware that has been targeting the financial services industry for the last couple of years. Like Emotet, TrickBot primarily spreads via email, though both banking trojans can also propagate via SMB file shares using the EternalBlue exploit.
Emotet got its start in 2014 as an unremarkable banking malware. Since then, it has undergone multiple iterations. Initially, the malware was delivered as a malicious JavaScript file, but later versions used macro-enabled documents, PDF files and weblinks to fetch malicious payloads from a C2 server. The banking trojan’s operators no longer simply maintain the malware; they also actively distribute malware for other attack groups, particularly the ones originating from Eastern Europe. Recently, attackers have begun using Emotet as a payload delivery mechanism for ransomware, information stealers, and other banking trojans including TrickBot, IcedID and Zeus Panda.
New Threats, New Strategy
What can be learned from this example? Malware exists within a complicated ecosystem. With so many interrelated and ever-evolving variants emerging constantly, it’s easy to lose sight of what’s happening in the bigger picture. But one thing we can count on is that cybercriminals will always seek easy money, and malware is a tool to that end. As with legitimate business models, the easiest way to make money is to leverage existing investments and successes. That’s the bigger picture of what we see here: cybercriminals using successful malware to expand business opportunities.
One particularly effective and dangerous example comes from a technique called malvertising. Many computer users today still think they have to click on a file or a link to be infected with malware, but that’s simply not the case. There are many ways for bad actors to deliver their malicious payload—from phishing emails to infecting legitimate websites with malicious scripts to the malvertising approach.
This approach makes use of the way most of today’s websites pull advertisements from multiple ad servers. If the bad guys can infect the ad server, their malware will be delivered to thousands of websites that are serving up that specific ad. This means any system connecting to a site with that ad—even without the user clicking on anything—will get infected. Usually, a malicious script will redirect the user to the attacker’s server where other malware or exploits are then downloaded.
In light of this and other malware threats, enterprises must reconsider their security strategy – particularly, if they are undergoing digital transformation. The first step is to identify and then eliminate as many points of weakness as possible. This includes a proactive inventory of devices, granular access control and dynamic network segmentation. Next, develop a proactive and integrated security approach that provides consistent protection across your entire distributed environment. In this way, you can better defend your entire network environment—from IoT devices and the mobile edge, the network core, the new WAN edge and out to multi-cloud environments—at speed and scale.
Higher (Threat) Intelligence
Because there will always be criminals ready to use and re-invent malware, cybersecurity will always need to be woven into every new infrastructure or technology initiative in your organization. This requires security to operate in an integrated and collaborative fashion to keep adversaries at bay. However, your security strategy will only be as effective as the data and threat intelligence that inform them. As cybercrime evolves, so will your cyber strategy. It’s an ongoing process that needs the most current and accurate information so you can adapt with agility.
Derek Manky is the Chief of Security Insights and Global Threat Alliances at Fortinet. In his role, he formulates the security strategy for the company. He is actively involved with several global threat intelligence initiatives, including NATO NICP, INTERPOL Expert Working Group, the Cyber Threat Alliance (CTA) working committee and FIRST, all in an effort to shape the future of actionable threat intelligence and proactive security strategy.
Disclaimer: CISO MAG does not endorse any of the claims made by the writer. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same. Views expressed in this article are personal.










