
CISO MAG recently hosted a Virtual Roundtable with Ajay Kumar, Director, Solutions Engineering of BeyondTrust, and Sean Gunasekera, ASEAN Cyber Security Lead, EY. The roundtable, which was moderated by Brian Pereira, Principal Editor, CISO MAG, was on the subject “Strengthening Operational Resilience Through a Universal Approach to Privilege Management.” A slew of cybersecurity experts comprising of CEOs, CISOs. CIOs, Vice Presidents, and executives from countries like the U.K, Singapore, Spain, Lebanon, Australia, India and even regions like Antigua and Barbuda attended the virtual roundtable.
The Panel
Gunasekera is a Partner and currently leads EY’s APAC Financial Services Cyber practice. He has spent the past 16 years in consulting, focusing on cyber security and cyber risk. His areas of expertise are in security strategy and operations.
Ajay Kumar has over 15 years of experience in cybersecurity, and seven specializing in privileged access and identity access management. Prior to becoming the Director of Solutions Engineering – APJ at BeyondTrust, he was the Regional Technical Sales Leader for over seven years at IBM. He is a trusted cybersecurity advisor to enterprise customers, his experience spans across several industries such as banking, insurance, energy, and utilities, in addition to state and federal government.
To reduce the impact of COVID-19, organizations had relocated their workforce to a remote operating model. The discussion began with the subject of COVID-19 impacting cybersecurity operations in the APAC region. Gunasekera took the lead on it and said, “Organizations have had to adjust on multiple fronts, business processes have had to change, and even sensitive business transactions had to be remotely.” He also suggested that technology operations also had to change to accommodate the shift in dynamics, like how a vendor who would have traditionally been onsite to do work on an air gapped system would have to be more relied on home working now. He stressed on how when business make concessions and allow for sensitive transactions to be done offsite cyber controls must be implemented to secure these transactions.
Gunasekera continued, “From an attack surface perspective, as organizations adapted their external perimeter controls to allow for remote access, we also saw an influx of attacks targeting this. Whether it was phishing attacks targeting people’s remote access credentials or country specific campaigns like the malware associated with fake contact tracing apps in Singapore.”
Kumar added, “Another one of the biggest challenges was to add VPN capacity across all breadth, as well as the emergence of shadow IT— applications and infrastructure that are managed and utilized without the knowledge of the enterprise’s IT department. Many a times companies did not know the volume of shadow IT within an organization.”
The virtual roundtable also addressed several other key topics like adoption of new technologies, and compromise of privileged accounts. Talking about the common mistakes made by IT and system admins while managing privileged accounts, Kumar said, “It begins from not changing the password often. Apart from that there is also a trend of account sharing amongst multiple administrators. Another common mistake is multiple accounts for multiple environments like Unix and Windows, which in turn increases the number of accounts and therefore the attack surface. And lastly, as organizations move into DevOps – it is essential that the API keys are appropriately secured.
The three key takeaways from the roundtable were:
- The adoption of new technologies has resulted in a proliferation of privileged credentials and the expansion of the privilege “universe”. This has compelled CISOs to adopt a new model for privileged access management. Password Management alone is no longer enough to secure the enterprise “privilege universe”.
- COVID-19 has forced CISOs to reconsider their cybersecurity models to improve operational resilience and security scalability/flexibility, that must now support and protect an increased remote workforce.
- Recommended by leading analyst and consultancy firms, Privileged Access Management is an essential component of an organization’s IT security strategy and their journey to meet compliance mandates such as MAS TRM, RMiT, PCI DSS and others.
Attendees of the roundtable also took part in a snap poll. Here are the results:


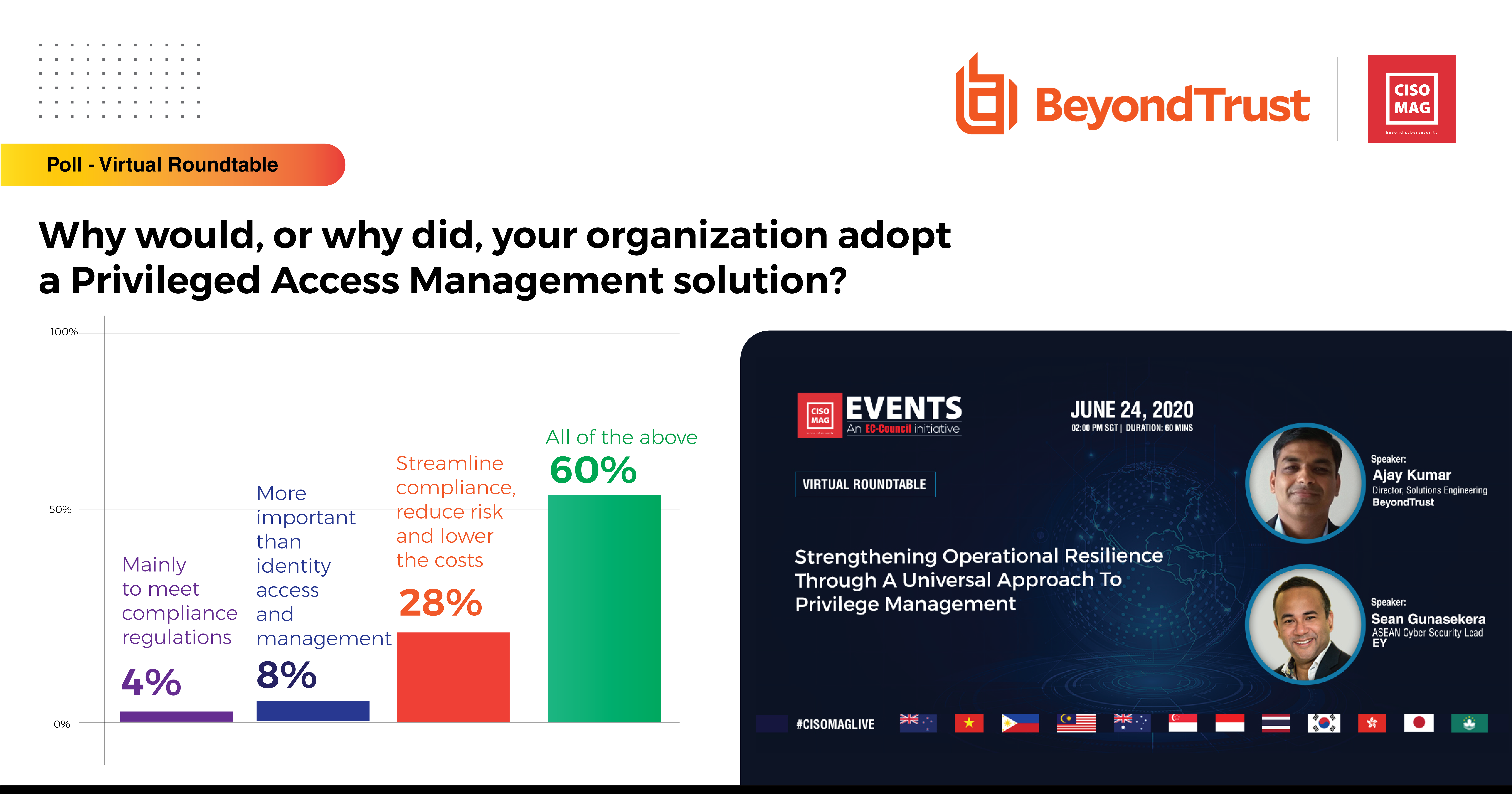 You can watch the entire recording of the Virtual Roundtable at: https://attendee.gotowebinar.com/recording/1726333718968954370
You can watch the entire recording of the Virtual Roundtable at: https://attendee.gotowebinar.com/recording/1726333718968954370
Through the Virtual Roundtable and Fireside Chat series, CISO MAG will be partnering with industry experts and solution providers from across the world to host similar webinars to discuss some of the pressing issues and trends in the cybersecurity. Stay tuned.
About BeyondTrust
BeyondTrust is the worldwide leader in Privileged Access Management (PAM), empowering organizations to secure and manage their entire universe of privileges. Our integrated products and platform offer the industry’s most advanced PAM solution, enabling organizations to quickly shrink their attack surface across traditional, cloud and hybrid environments.
The BeyondTrust Universal Privilege Management approach secures and protects privileges across passwords, endpoints, and access, giving organizations the visibility and control they need to reduce risk, achieve compliance, and boost operational performance. We are trusted by 20,000 customers, including 70 percent of the Fortune 500, and a global partner network. Learn more at www.beyondtrust.com.
About CISO MAG
CISO MAG is a publication from EC-Council, which provides unbiased and useful information to the professionals working to secure critical sectors. The information security magazine includes news, comprehensive analysis, cutting-edge features, and contributions from thought leaders, that are nothing like the ordinary. Within the first year of launch, the magazine reached a global readership of over 50,000 readers. The magazine also has an Editorial Advisory Board that comprises some of the foremost innovators and thought leaders in the cybersecurity space. Apart from this, CISO MAG also presents a platform that reach out to the cybersecurity professionals across the globe through its Summits and Awards and Power List surveys.
About EC-Council
EC-Council, officially incorporated as the International Council of E-Commerce Consultants, was formed to create information security training and certification programs to help the very community our connected economy would rely on to save them from a devastating Cyberattack. EC-Council rapidly gained the support of top researchers and subject matter experts around the world and launched its first Information Security Program, the Certified Ethical Hacker. With this ever-growing team of subject matter experts and InfoSec researchers, EC-Council continued to build various standards, certifications and training programs in the electronic commerce and information security space, becoming the largest cybersecurity certification body in the world. Learn more at https://www.eccouncil.org.










