
– Popular outdoor clothing and accessories retailer – “The North Face” – was hit by a credential stuffing attack on October 8 & 9.
– Apart from email IDs and passwords, the retail giant believes users’ PII (personally identifiable information) and store purchase history may have been accessed by the cybercriminals.
What Happened in the North?
According to the data breach notification, the company said that it was “alerted to an unusual activity” involving its website, thenorthface.com, on October 9, 2020. To clear the growing suspicion, the company’s IT team conducted a thorough internal investigation. Through this, it found conclusive evidence that cybercriminals were targeting its customers through a credential stuffing attack on their website. The North Face immediately took responsive measures by resetting an undisclosed number of customer accounts.
How Does a Credential Stuffing Attack Work?
Credential stuffing is a malicious activity where cybercriminals take advantage of people reusing the same passwords across multiple online accounts. It is like a single key working across multiple locks.
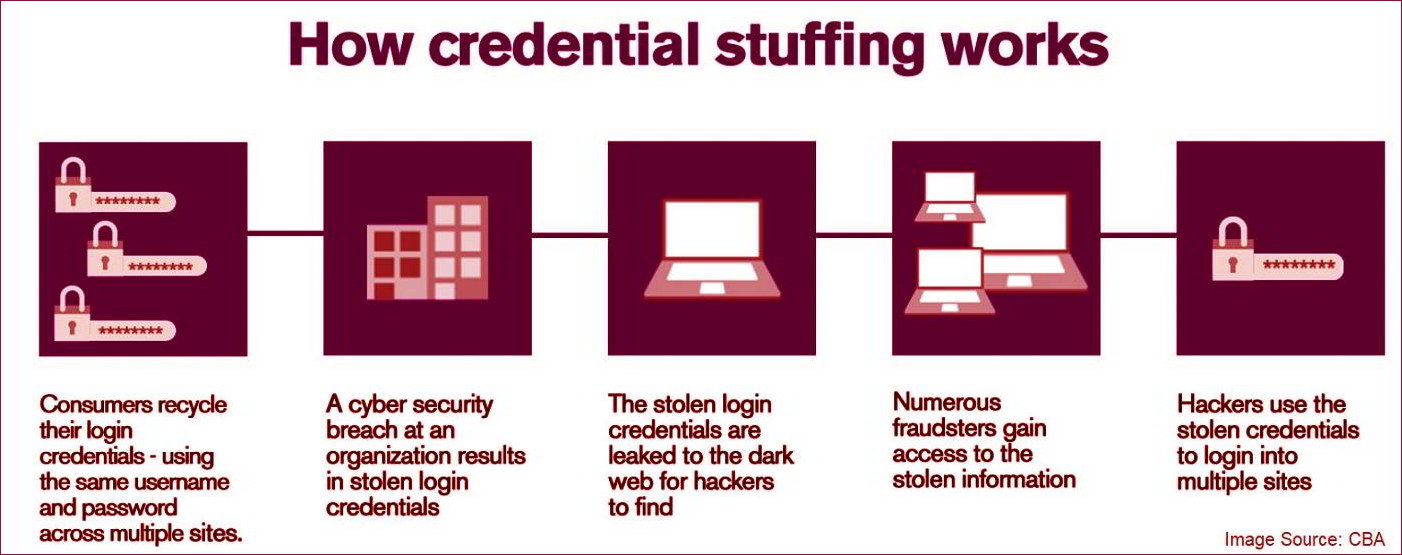
However, this attack vector only works when passwords and/or other PII are reused by users for more than one account. These PII and passwords are typically stolen from another source, such as a data breach of another company or website, and then with the help of botnets are “stuffed” and tested across various popular websites. This is exactly what happened in the case of “The North Face”, thus, resulting in unauthorized access of cybercriminals into its specific data set.
Related News:
Hackers Target Loyalty Programs to Obtain Users’ Sensitive Data
As mentioned earlier, apart from the email IDs and passwords, it is possible that cybercriminals have accessed users’ purchase information that includes, billing and shipping address, VIPeak customer loyalty point total, email preferences, first and last name, birthday (if it was saved), and telephone number (if it was saved). This information, however, did not contain any payment card (credit/debit) details including the card CVV number, as it was never saved on thenorthface.com website.
How to Avoid Credential Stuffing Damages
Although The North Face claims that none of the critically valuable information was leaked from their end, it is possible that some of the PII was leaked in an earlier data breach from where these stolen credentials were used in the first place. So, how do we avoid any damages from a credential stuffing attack?
The first and the best line of defense against credential stuffing attack is using a unique password for every account across the internet. Do not recycle and reuse same password across all website as a breach in one of the accounts could potentially compromise the safety of all your accounts.
Tips to create a strong and unique password for each account
- Use at least one UPPERCASE and one lower case letter
- Use at least one (0,1,2,3,4,5,6,7,8,9)
- Use at least one special character (such as “!,” “%,” or “$”)
- Use a minimum of 8 characters in your password
- In case of creating and remembering passwords for multiple accounts,
- Create a strong base password using above rules (Example: 8$ciTeK#).
- Use part of the account URL at a start or end of the base password (Example for Facebook: FB8$ciTeK# or 8$ciTeK#FB or F8$ciTeK#B).
Credential stuffing has become a serious issue in recent years and its evidence is provided by a recent report from Akamai which found that more than 100 billion credential stuffing attacks took place between July 2018 and June 2020. Thus, it is time to act now and act quickly. Using the tips provided above may not be full-proof but it surely raises your protection shield a bit higher than it was earlier.
Related News:
Media Industry Becomes a Common Ground for Credential Stuffing Attacks










