
Apple is known for its airtight security across its product line. However, a mystery malware dubbed “Silver Sparrow” has broken this myth by infecting nearly 30,000 Macs (29,139 to be precise) in over 153 countries worldwide. Researchers are scratching their heads trying to understand this malware because it is hiding on the infected machines still waiting for a payload to arrive. Usually, post-compromise, a payload is dropped that then carries out malicious activities, however, this is not the case here.
Analyzing the Silver Sparrow Malware
Red Canary’s blog post offers an in-depth analysis of how the malware was discovered, its targets, operations, and how it affects Apple’s latest M1 chip. For those who want facts and figures, the Silver Sparrow malware is currently the second known malware targeting the Apple M1 silicon chip. The first one was incidentally discovered a week ago by security researcher Patrick Wardle from Objective-See.
As per Red Canary, the Silver Sparrow malware has two versions:
- Version 1 IOCs
File name: updater.pkg (installer package for v1)
MD5: 30c9bc7d40454e501c358f77449071aa
- Version 2 IOCs
File name: update.pkg (installer package for v2)
MD5: fdd6fb2b1dfe07b0e57d4cbfef9c8149
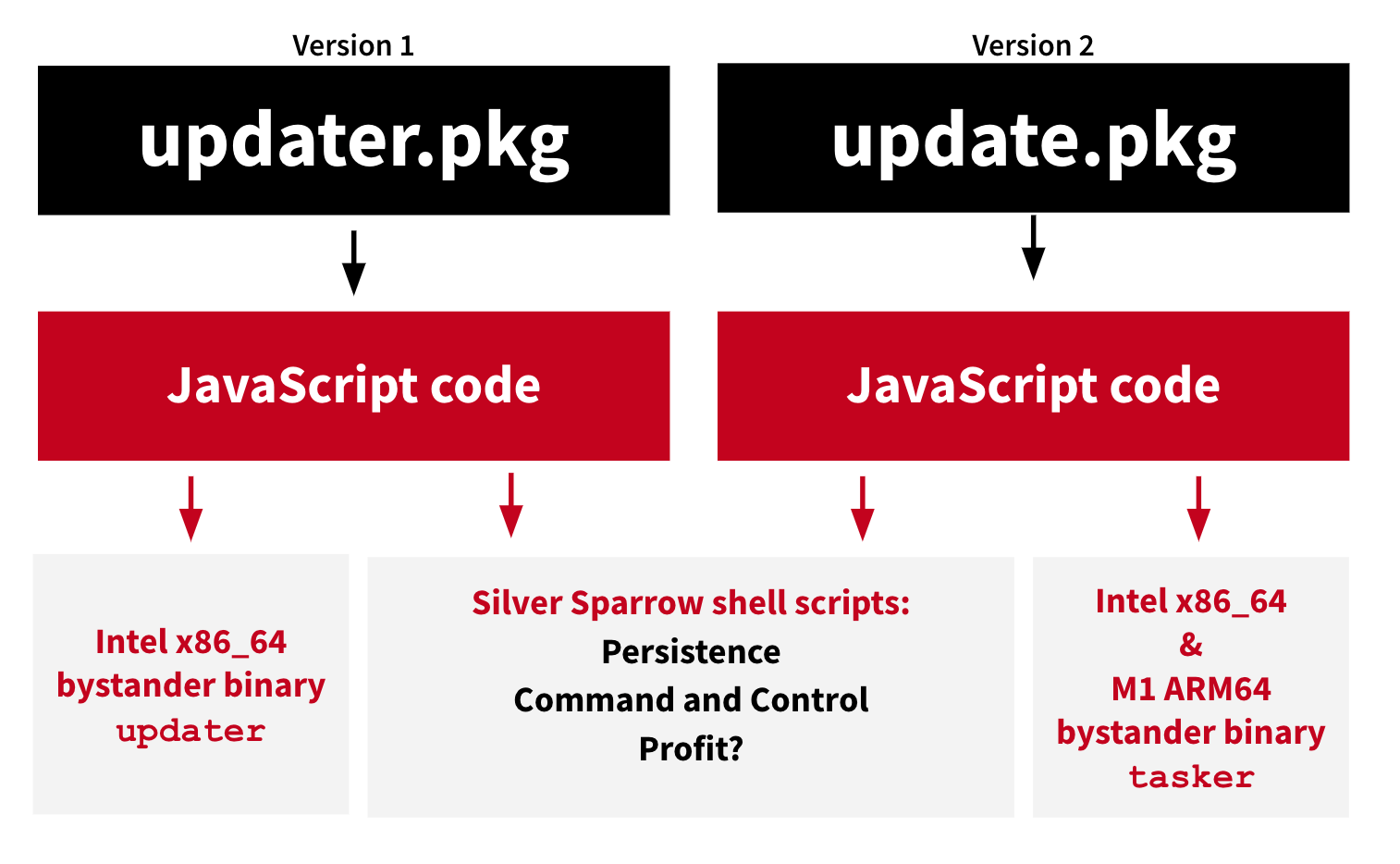
As shown in the above image, one version is a binary in mach-object format compiled for Intel x86_64 processors and the other version is a Mach-O binary for the M1 chip. The researchers believe that these are “bystander binaries” as they only display messages like “Hello World!” and “You did it!” when executed. As precautionary measures, Apple has revoked the licenses of both the binaries effective immediately.
Related News:
TeamTNT Spreads Malware with New Detection Evasion Tool “Libprocesshider”
Silver Sparrow uses Apple’s system.run command for execution and is thus difficult to detect. Researchers found that every hour the malware contacts the command-and-control center (C2) for further actions, however, none have been observed until now keeping the malware in stealth mode. Another interesting mechanism that the Silver Sparrow malware contains is its self-destruct mode. It has a file check that causes removal of all persistence mechanisms and scripts on execution leaving behind no trail of the attack vectors. Researchers say that the presence of such a sophisticated mechanism for this malware is also a “mystery,” because it means that the attackers were getting ready for a stealthy persistent attack rather than a simple intrude, spread, and exfiltrate kind of attack.
Thankfully, there is still no known indication of any damages through this malware, but the fact that Red Canary’s researchers found these strains of malware on Macs in the wild is worrisome. For the complete list of IOCs of the Silver Sparrow malware, click here.
Related News:
Researcher Finds New Android Malware Spreading Via WhatsApp Messages










