
Security experts from Malwarebytes discovered a new malware strain used in phishing attacks to install credential stealers and additional malware payloads. Tracked as Saint Bot, the malware poses a wide variety of sophisticated techniques across the infection stages, including anti-analysis tactics, process injection, and command and control infrastructure and communication.
Discovery of Saint Bot Malware
Malwarebytes researchers stated that they found a phishing email in late March 2021, with a ZIP file attachment that contained a PowerShell script disguised as a link to a Bitcoin wallet. The researchers further found that the obfuscated PowerShell downloader initiates the infection process by deploying Saint Bot malware, which was used in various COVID-19 themed phishing campaigns against government and private enterprises globally.
Saint Bot Capabilities
Saint Bot has additional capabilities such as malware stealers including Taurus and AutoIt. “Its design allows to utilize it for distributing any kind of malware. Although currently, it does not appear to be widespread, there is an indication that it is being actively developed. Furthermore, Saint Bot employs a wide variety of techniques which, although not novel, indicate some level of sophistication considering its relatively new appearance,” Malwarebytes said.
How does Saint Bot spread?
Saint Bot is mostly distributed in a malicious ZIP file attachment bitcoin.zip, luring the victim to get to a Bitcoin wallet. Once the victim opens the file, it provides a pair of files: a .lnk file that leads to a Bitcoin wallet and a .txt file that claims to be a password to the wallet.
Once opened, the .lnk file redirects the user to C:\Windows\System32\cmd.exe, which contains a malicious PowerShell script that downloads the next stage of the malware from the embedded link. Once the malware is implanted successfully, it connects to its Command-and-Control server (C2) and proceeds with its main actions
Delivery Path
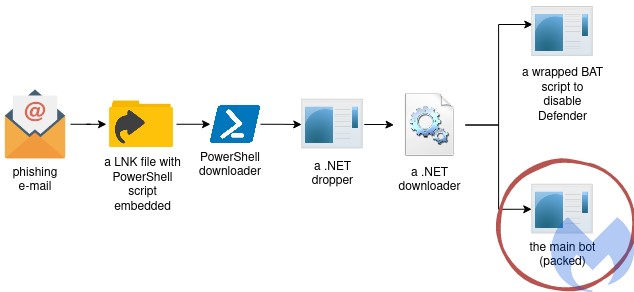
Execution Flow
- Install itself
- Inject itself into EhStorAurhn.exe
- Communicate with the C2 and proceed with the main operations
“Saint Bot is yet another tiny downloader. We suspect it is being sold as a commodity on one of the darknet forums, and not linked with any specific actor. The author seems to have some knowledge of malware design, which is visible by the wide range of techniques used. Yet, all the deployed techniques are well-known and pretty standard, not showing much creativity so far. Will it become the next widespread downloader or disappear from the landscape, pushed away by some other, similar products? We have yet to see,” Malwarebytes added.










