
The unprecedented rise of cloud technologies, and the emergence of the Internet of Things (IoT) and Software Defined Networks (SDN) have accelerated the digitization of businesses. The very fabric of traditional business methodologies has been transformed by advanced data-driven technologies that elevate business growth to the next level. However, one thing that has grown together with the digital revolution in recent years is the compliance and regulatory landscape, and a parallel need for a comprehensive breach readiness plan.
The impact that personal data protection, compliances, and regulators such as Canada’s PIPEDA (Personal Information Protection and Electronic Documents Act) and European Union’s GDPR (General Data Protection Regulation) have had on data privacy is humongous, and the numbers do not lie, as we see next.
Recap through Numbers
According to the observations mentioned in a blog named, “A full year of mandatory data breach reporting,” the Office of the Privacy Commissioner of Canada (OPC), reported a six-fold increase accounting to a total of 680 data breaches since PIPEDA’s implementation on November 01, 2018. Here are some other observations from the year:
- Overall, 28 million Canadian citizens were affected by these data breaches which included known headline-grabbers like LifeLabs, Desjardins and Capital One.
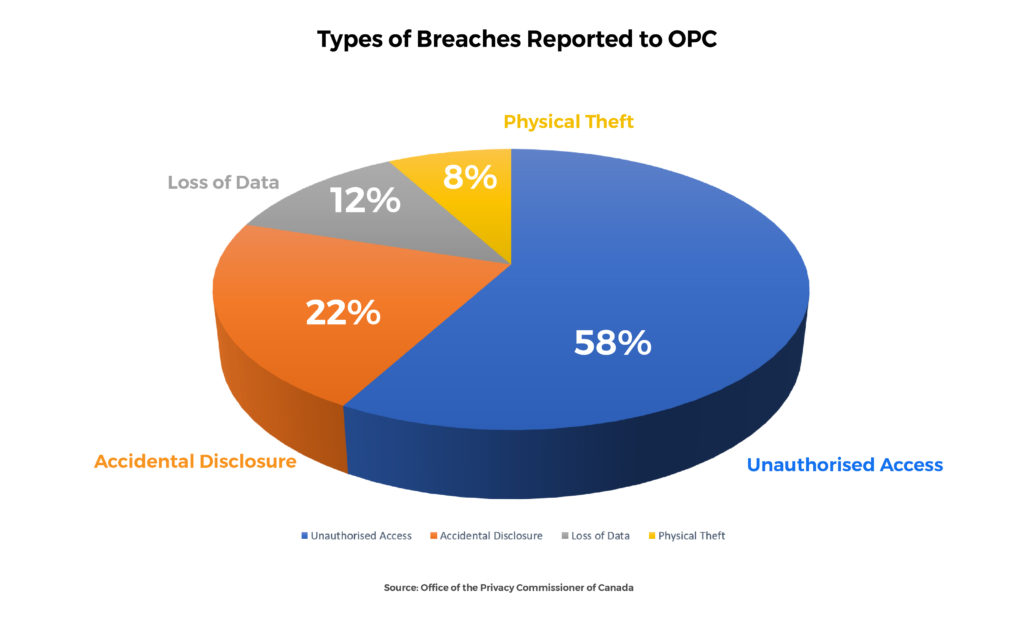
- Of the 680 breaches reported to the OPC:
- 397 were due to Unauthorized Access
- 147 were from Accidental Disclosure
- 82 of them accounted for Physical Loss
- 54 of the breaches were due to Physical Theft of things
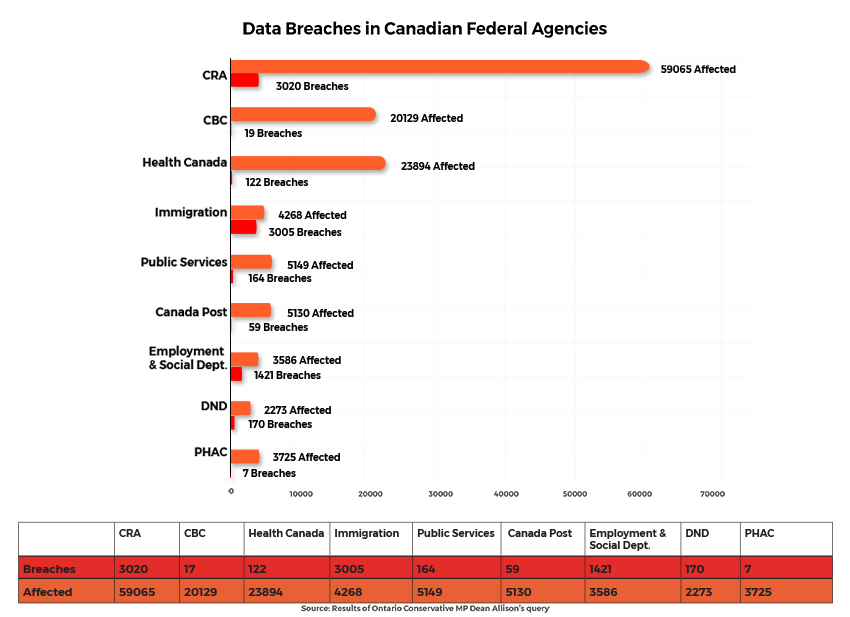
PIPEDA addresses the responsibilities of non-public organizations in disclosing data breaches of personal information. However, in a recent record tabled in the House of Commons in response to an order paper question filed by Conservative MP Dean Allison, it has come to light that personal information belonging to 144,000 Canadians has been mishandled by federal departments and agencies over the past two years. The nearly 800-page response not only underlines the lack of cybersecurity practices of federal agencies but also exposes their lack of a breach readiness plan. Other statistics that include records between January 2018, and December 2019 are as follows:
- In total, 7,992 breaches were found to have occurred at 10 different agencies and departments.
- The Canada Revenue Agency (CRA) was the worst offender, with 3,020 breaches affecting nearly 60,000
- Health Canada reported 122 breaches affecting close to 24,000
- Canadian Broadcasting Company (CBC) was breached 17 times and data of 20,000 employees was leaked.
- The Canadian Immigration Department recorded a very high volume of data breaches accounting to 3,005 instances, affecting 4,268
Cybersecurity Awareness a Big Problem for Canadians
Canadian Internet Registration Authority (CIRA) is a non-profit organization that manages the [.]CA domain name registry on behalf of Canada. Its Cybersecurity Survey 2019, found that 71% of the organizations in Canada reported at least one cyberattack in the past year, and yet, only 41% of its respondents had mandatory cybersecurity awareness training in place for its employees. The lack of basic cybersecurity education has a ripple effect as it feeds the organization’s reputational risks.
Another example of Canada’s complacency towards cybersecurity and personal data security can be found in a survey conducted by the credit bureau, Equifax. For instance, 92% of the survey respondents agreed that online fraud and identity theft is a serious issue. However, only 29% of them said they checked their credit report over the last 12 months to help protect their personal data, and surprisingly, only 38% of them indicated they would report fraud to a credit bureau. The data also revealed a contradictory picture as Canadians now feel less vulnerable to fraudsters online (80% in 2019 to 72% in 2020), on-the-go (59% in 2019 to 44% in 2020), at home (37% in 2019 to 27% in 2020), and in-store (38% in 2019 to 25% in 2020) as compared to the year before. So how do we address the elephant in the room?
- Breach Preparedness Plan – Choose a knowledgeable person to lead the Breach Preparedness and Response Team, someone like a CISO, CIO, or CO (Compliance officer). The team should consist of members with special skill sets mainly including IT security, legal and public relations, and privacy experts. Have a data breach or cyber insurance policy to cover all the losses and expenses in case of a cyberattack. Also implement the best-suited cybersecurity technologies for your business, like anti-virus, intrusion detection and prevention system, etc.
- Train your Employees – Even those having a basic knowledge of cybersecurity might not be updated with the evolving threat vectors. Thus, invest in your employee’s cybersecurity training and make them aware of various aspects of data hygiene such as proper handling and storage of data, role-based data access levels, latest scams and threats to be aware of, SOPs and reporting procedures in case of a data breach, etc.
- Perform Risk Assessments – Conduct scheduled risk and vulnerability assessments. Perform penetration testing to ensure timely threat identification. Focus on the entire operations and supply chain, including third parties collecting personal information of your employees and customers. Identify and fill-up the cracks in your security before a breach exploits it.
- Stay Alert and Updated of Other Breaches – Stay updated with the latest breaches related to your business segment. Threat actors prefer re-use of the same attack vectors against multiple organizations in a similar industry. Subscribe to alerts and newsletters from your industry’s association and other sources of news.
Although these risk mitigation steps lower the risk of a data breach and loss of one’s digital identity, an important question still persists: It isn’t about if your data will be compromised, but when? So, what does one do in the case of a cyberattack or a data breach episode? The answer is Incident Response Plan.
Incident Response – Dialing Plan Z for Crisis Management
Prompt incident response or crisis management is very important for any organization and it should mainly focus on the following five steps:
- Containment – Don’t let it spread. The moment you detect a breach, terminate any or all unauthorized practices, recover as much data as possible, shut down the system and isolate the network that was breached; perform a mandatory password reset for all employees and customers, and patch all vulnerabilities in physical or electronic security.
- Investigation – Ask your breach response team to lead the initial breach investigation. They should have the appropriate authority and knowledge to conduct the initial investigation and make recommendations. If necessary, a more detailed investigation may subsequently be undertaken from external cybersecurity experts.
- Notification – Determine who needs to be made aware of the incident internally, and externally, at the preliminary stage. Escalate internally to inform the person within your organization who is mainly responsible for privacy compliance. And above all do not hide anything; tell the truth.
- Preservation – Be careful not to destroy evidence that may be valuable in determining the cause of the breach or allows you to take appropriate corrective measures.
- Restoration – Support your customer. Even before you restore your systems, start rebuilding customers’ faith. If the data breach affects one of your online services, then make sure to focus on this as a separate and important issue. Ignoring your customers’ problems can quickly turn this situation into a reputation risk and not only tarnish the brand name but eventually lead to loss of business and revenue.
In the current scenario, it is not as if businesses do not take adequate cybersecurity measures or follow best practices. The fact is, the threat landscape is evolving at a faster pace than many predicted. Thus, safeguarding and securing the digital identities of both, employees and customers are putting businesses under significant strain. Add to that the worry of failed compliance audits, large overhead costs, limited pool of skilled workforce, and a weak digital identity management. They all contradict the recommendations of a regulatory body like PIPEDA and hence, a data breach and loss of digital identity are considered inevitable.
However, the answer to these problems lies in the questions itself. Breach preparedness with an incident response plan is highly recommended in such situations. And for this, we look at turnkey solutions like ID AssistTM.
About ID AssistTM
ID AssistTM is an online identity theft monitoring solution provider. This breakthrough platform simplifies your digital identity monitoring and restoration process in case of a data breach. Its immediate deployment facilitates businesses to limit their brand’s reputation risks and controls potential damages to your customers. Additionally, it provides monitoring from both Canadian Credit Bureaus — Equifax® and TransUnion® —to its customers.
Other Features
- 24/7 Monitoring – It includes credit and/or debit cards, chequing and/or savings account numbers, social insurance number, driver’s license number, passport numbers, email addresses, and phone numbers.
- Fraud Alerts – Alerts the customers of any suspicious activity to minimize the damage and resulting stress. Correspondingly, ID AssistTM also contacts Equifax Canada and TransUnion Canada on your behalf to have an alert placed on your file.
- Monthly Credit Score and Quarterly Credit Report – Provides a full snapshot of a customer’s financial history from Equifax to keep track of their credit standing and any unexpected changes or credit inquiries.
- Guided Restoration – A dedicated Fraud Investigator will confirm your identity was stolen, put all the pieces back together, complete all the paperwork, and follow up with the respective agencies and the victim throughout the process.
Emerging technologies, stricter compliances, limited pool of skilled resources, and dubious ROIs are straining business models to the optimum. It is creating visible cracks in the physical, virtual, and network infrastructures of many organizations. Cybercriminals are exploiting these gaps and further adding to the strain. However, a smart breach readiness plan including specialized services like ID AssistTM helps in minimizing this strain. It not only enhances and adheres to the cybersecurity and compliance needs of the organization but safeguards your brand reputation and customer and employees’ digital identities.
Start your breach readiness plan today – make sure your organization is ready with ID Assist.
Disclaimer
CISO MAG did not evaluate the advertised/mentioned product, service, or company, nor does it endorse any of the claims made by the advertisement/writer. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.










