Researchers at Forescout Research Labs, with support from Medigate Labs, discovered vulnerabilities affecting Nucleus TCP/IP stack, a software that powers devices across the health care system. The lab has discovered a set of 13 new vulnerabilities, which could lead...
Cybercriminals often leverage Distributed Denial of Services (DDoS) techniques to disrupt critical services of global organizations. Days after a massive DDoS attack on multiple voice over internet protocol (VoIP) services in the U.K., Telnyx reported that it had suffered...
Cloud computing security (CCS) is an essential aspect for businesses when securing virtual data, however, like any other domain within IT security, it comes with its challenges. Being a shared and hybrid operation framework, business and security leaders along...
Microsoft has released patches for over 55 security vulnerabilities in its latest November 2021 Patch Tuesday update. Six of these vulnerabilities are rated as critical and 49 as important in terms of severity. The update has addressed security flaws...
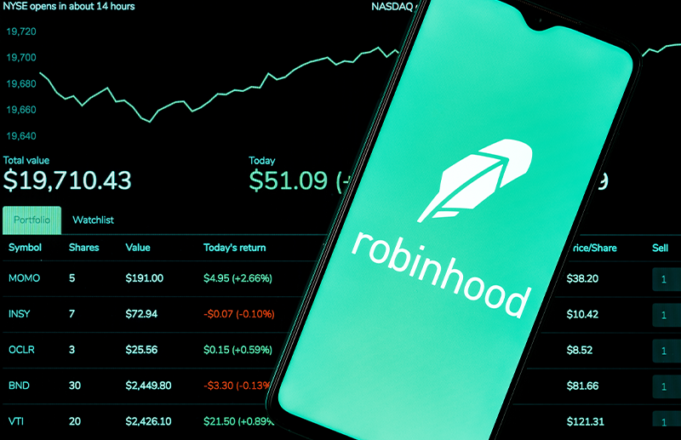
Robinhood, a commission-free, U.S.-based trading app, joins the list of ransomware victims. On November 3, 2021, the trading platform experienced a phishing attack in which a customer support employee fell prey to the ransomware trap. As a result, data...
India’s popular securities depository services provider - the Central Depository Services Limited (CDSL) - is making headlines for an alleged data breach at its subsidiary CDSL Ventures Limited (CVL). According to a report from CyberX9, the data breach exposed...
What are some of the biggest challenges facing countries across the globe today? Technology is transforming human societies and communities across the globe, in different ways, changing the way we live and conduct business. As its pervasiveness becomes a...
Threat actors leverage Trojans, malware, and ransomware to break into victims’ systems and cause maximum damage. We explain a different kind of malware threat that impacts users’ data privacy and security – Rootkits. Cybercriminals often utilize rootkits to spy...
Critical infrastructure and technology vendors become a frequent target for state-sponsored adversaries. A security research team from Palo Alto Networks’ Unit 42 uncovered an ongoing cyberespionage campaign that has already targeted nine organizations belonging to critical global sectors, including...
Cyber intrusion activity globally jumped 125% in the first half of 2021 compared to the previous year, according to Accenture, with ransomware and extortion operations one of the major contributors behind this increase. According to the FBI, there was...