Call it an act of bittersweet revenge. A victim of the Muhstik Ransomware attack who had to pay up the hackers for releasing his data went right back at the hackers by hacking them (him/her) back, and even released...
In a bid to provide interoperability and data-sharing across several cybersecurity products and companies, IBM Security and McAfee are spearheading an open-source cybersecurity alliance along with 14 other cybersecurity companies across the globe.
The new Open Cybersecurity Alliance (OCA) will...
Cybersecurity has been at a nascent stage for several states in the United States. With the California Consumer Privacy Act (CCPA) around the corner, you would imagine that other states are sprucing up cybersecurity in their region and are...
Razberi Technologies, a provider of simple and secure IoT solutions, recently raised US$ 5.8 million in an investment round led by LiveOak Venture Partners along with the participation from Chartline Capital Partners and other investors.
Doug Dickerson, the CEO of...
By Benjamin Donnelly
Let me be clear. The types of hackers that we’ve been seeing have rapidly changed in the past five or so years. There is a clear trend that only a few highly informed individuals have been following. ...
By Sanjay Aurora, Managing Director, Asia Pacific, Darktrace
As the near-constant stream of high-profile attacks suggests, the cyber-threat landscape is rapidly evolving with no sign of slowing. Cyber-attackers are not only moving faster, they are adding new...
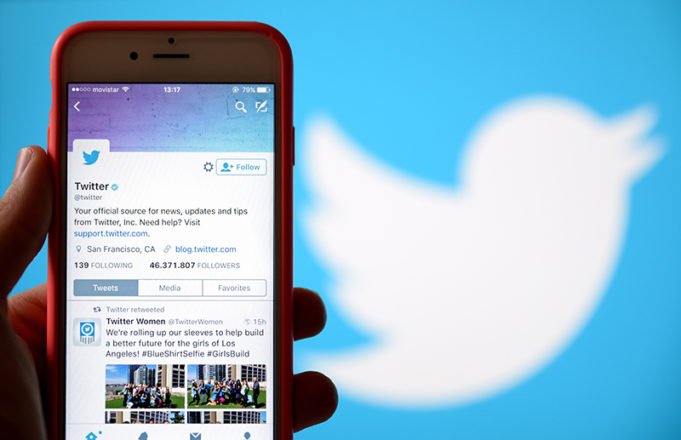
A security blunder by Twitter exposed phone numbers and email addresses of its users who opted for two-factor authentication (2FA) protection. The social networking company stated that user contacts had been used for targeted advertising purposes.
In an official statement,...
Trend Micro, a cybersecurity and defense company, recently announced a strategic partnership with the developer-first security company Snyk to help businesses cope with potential vulnerabilities without interrupting the software delivery process.
The new alliance integrates open source vulnerability intelligence from...
Security researchers exposed an unpatched Zero-Day flaw in Android devices. The flaw, which was discovered under active exploitation, targets most of the Android smartphones from popular brands.
According to Google’s Project Zero researcher Maddie Stone, the vulnerability named CVE-2019-2215 could...
By Brian Pereira
CERT-In is the Indian Chapter of the global Computer Emergency Response Team (CERT), and it has been in existence since 2004. The Indian Information Technology Amendment Act 2008 denotes CERT-in as the national agency to perform various...