
Security incidents occur. It’s not a matter of ‘if’ but of ‘when.’ There are security products and procedures that were implemented to optimize the IR process, so from the ‘security-professional’ angle, things are taken care of.
SPONSORED CONTENT
By George Tubin, Director of Product Strategy at Cynet
However, many security pros who are doing an excellent job in handling incidents find effectively communicating the ongoing process with their management a much more challenging task.
It’s a little surprise — managements are typically not security savvy and don’t really care about the bits and bytes in which the security pro masters. Cynet addresses this gap with the IR Reporting for Management PPT template, providing CISOs and CIOs with a clear and intuitive tool to report both the ongoing IR process and its conclusion.
The IR for Management template enables CISOs and CIOs to communicate with the two key points that management cares about — assurance that the incident is under control and a clear understanding of implications and root cause.
Control is a key aspect of IR processes, in the sense that at any given moment, there is full transparency of what is addressed, what is known and needs to be remediated, and what further investigation is needed to unveil parts of the attack that are yet unknown.
Management doesn’t think in terms of Trojans, exploits, and lateral movement, but rather it thinks in terms of business productivity — downtime, man-hours, loss of sensitive data.
Mapping a high-level description of the attack route to resulted damage is paramount to get the management’s understanding and involvement, especially if the IR process entails additional spending.
The Template follows the SANS\NIST IR framework and comprises the following stages:
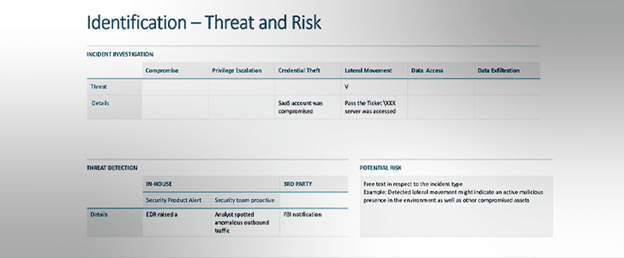
Identification
Attacker presence is detected beyond doubt. Was the detection made in house or by a third party, how mature the attack is (in terms of its progress along the kill chain), what is the estimated risk, and will the following steps be taken with internal resources, or is there a need to engage a service provider?
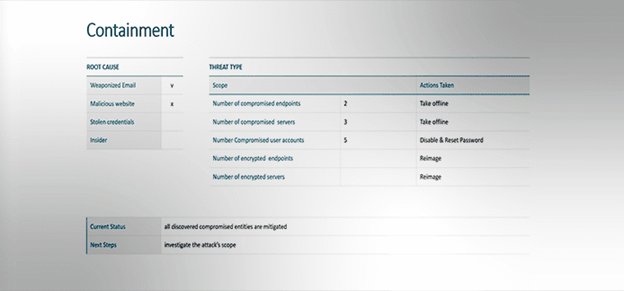
Containment
First aid to stop the immediate bleeding before any further investigation, the attack root cause, the number of entities taken offline (endpoints, servers, user accounts), current status, and onward steps.
Eradication
Full clean-up of all malicious infrastructure and activities, a complete report on the attack’s route and assumed objectives, overall business impact (man-hours, lost data, regulatory implications, and others per the varying context).
Recovery
Recovery rate in terms of endpoints, servers, applications, cloud workloads, and data.
Lessons Learned
What were the attack’s enablers (lack of adequate security technology in place, insecure workforce practices, etc.), and how they can be mended, and reflection on the previous stages across the IR process timeline searching for what to preserve and what to improve.
Naturally, there is no one-size-fits-all in a security incident. For example, there might be cases in which the identification and containment will take place almost instantly together, while in other events, the containment might take longer, requiring several presentations on its interim status. That’s why the template is modular and can be easily adjustable to any variant.
Communication to management is not a nice-to-have but a critical part of the IR process itself. The definitive IR Reporting to Management PPT template enables all who work hard to conduct professional and efficient IR processes in their organizations to make their efforts and results crystal clear to their management.
Download the Definitive IR Reporting to Management PPT template here.
About the Author
 George Tubin is the Director of Product Strategy at Cynet and a recognized expert in cybercrime prevention. He was previously VP of Marketing at Socure and Senior Research Director at TowerGroup where he delivered thought leadership and insights to large enterprises on cybersecurity as well as identity and fraud management.
George Tubin is the Director of Product Strategy at Cynet and a recognized expert in cybercrime prevention. He was previously VP of Marketing at Socure and Senior Research Director at TowerGroup where he delivered thought leadership and insights to large enterprises on cybersecurity as well as identity and fraud management.
DISCLAIMER
Views expressed in this article are personal. The facts, opinions, and language in the article do not reflect the views of CISO MAG and CISO MAG does not assume any responsibility or liability for the same.










