
International law enforcement authorities and the cybersecurity community are joining hands to thwart evolving cyberattacks from various threat actors operating across the globe. Recently, the FBI and the Australian Cyber Security Center (ACSC) warned about the ongoing Avaddon ransomware campaign targeting manufacturers, airlines, and health care organizations globally.
Avaddon Ransomware
The Avaddon ransomware variant was first spotted in February 2019. The ACSC claimed that the Avaddon ransomware variant is leveraged as a Ransomware-as-a-Service (RaaS) in several cybercriminal campaigns in Australia. Operators behind Avaddon usually demand a ransom payment in Bitcoin (BTC), with an average demand of BTC 0.73 (approximately $40,000) for a decryption key.
“Avaddon has an active presence on underground dark web cybercrime forums, notably advertising the Avaddon RaaS variant to potential affiliates via a number of high tiers cybercrime forums. Avaddon threat actors also utilize the data leak site (DLS) avaddongun7rngel[.]onion to identify victims who fail or refuse to pay ransom demands,” the ACSC said.
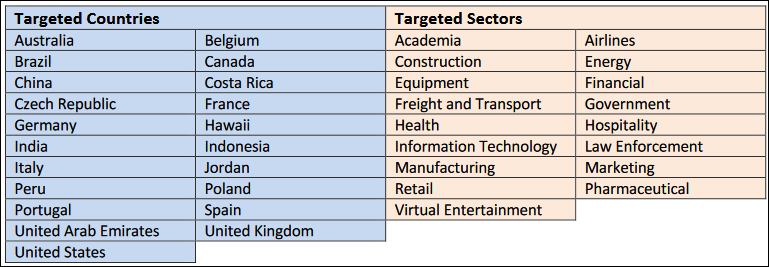
Avaddon Targeted Countries and Sectors
TTPs of Avaddon Ransomware Group
- Using phishing and malicious email spam campaigns to deliver malicious JavaScript files. These are often low in sophistication, containing a threat suggesting the attached file contains a compromising photo of the victim.
- Using double extortion techniques as coercion and further pressure victims to pay a ransom
- Threatening to publish the victim’s data (via the Avaddon Data Leak Site (DLS): avaddongun7rngel[.]onion
- Threatening the use of DDoS attacks against the victim
How does Avaddon attack?
According to security firm Trend Micro, Avaddon downloads the ransomware from malicious sites and deploys them on critical systems. The ransomware is distributed via emails with mostly fake photo attachments named IMG{6 random number}.jpg.js.zip, which also contains a JavaScript file named IMG{6 random number}.jpg.js. Once the user downloads the attachment, the malware automatically downloads and runs the ransomware payload. The ransomware then encrypts the critical files in the system and appends them with the .avdn file extension.
A ransom note is displayed on the victims’ system, which reads: “All your files have been encrypted.”
Mitigation Measures
The ACSC also recommended certain security measures for improved security:
- Patch operating systems and applications, and keep antivirus signatures up to date.
- Scan emails and attachments to detect and block malware and implement training and processes to identify phishing and externally sourced emails.
- Maintain offline, encrypted backups of data and regularly test your backups.
- Regularly conduct backup procedures and keep backups offline or in separate networks.
Related Story: How Australia Plans to Thwart Ransomware Attacks










