
Security experts from research firm vpnMentor discovered a data breach that exposed tens of thousands of private data belonging to CallX, a California headquartered telemarketing company. vpnMentor claimed that CallX failed to secure audio recordings, chats, and text transcriptions from its clients. The security incident exposed more than 100,000 private files online, making them publicly accessible.
Most of the exposed files include audio recordings of phone conversations, transcripts from over 2,000 text chats, conversations between CallX clients and their customers, along with customers’ private data, including, full names, phone numbers, home addresses, and callback dates for phone calls.
Threat Summary:
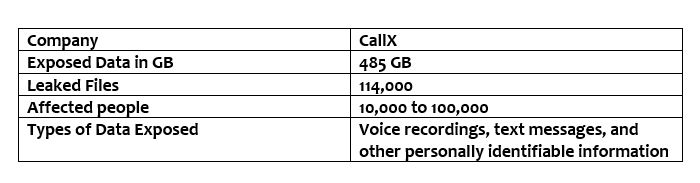
What caused the data leak
vpnMentor’s researchers stated that CallX used an unsecured Amazon Web Services (AWS) S3 bucket to store audio files of its client. vpnMentor notified the data leak to CallX authorities to fix the issue.
“Our team discovered CallX’s S3 bucket and was able to view it due to insufficient security. We found an image of the company’s logo amongst the files stored on the S3 bucket and, upon further investigation, confirmed the company as its owner. AWS S3 buckets are a popular form of enterprise cloud storage, but users must set up their own security protocols. Many companies using AWS are not aware of this,” vpnMentor said.
How to Secure an Open S3 Bucket
vpnMentor also recommended certain security measures to boost Open S3 Bucket security. These include:
- It’s important to note that publicly viewable S3 buckets are not a flaw of AWS. They’re usually the result of an error by the owner of the bucket. Amazon provides detailed instructions to AWS users to help them secure S3 buckets and keep them private.
- In the case of CallX, the quickest way to fix this error would be to make the bucket private and add authentication protocols.
- Follow AWS access and authentication best practices.
- Add more layers of protection to their S3 bucket to further restrict who can access it from every point of entry.










