
Samuel Grob, a security researcher at Google Project Zero, uncovered a new security feature that Apple added in its iOS 14 version without any revelation. Dubbed “BlastDoor,” the improved sandbox system feature was introduced due to the zero-click exploits that leveraged the Apple iMessage flaw in iOS 13.5.1. Reportedly, iPhones of 36 Al Jazeera journalists were infected with malware, leaving their devices open to cyber espionage.
The introduction of BlastDoor is a major change in iOS 14. BlastDoor is a tightly sandboxed service responsible for parsing untrusted data in iMessage.
“One of the major changes in iOS 14 is the introduction of a new, tightly sandboxed BlastDoor service which is now responsible for almost all parsing of untrusted data in iMessages. Furthermore, this service is written in Swift, a (mostly) memory-safe language which makes it significantly harder to introduce classic memory corruption vulnerabilities into the code base,” Grob said.
How BlastDoor Works
Grob stated that BlastDoor possesses a variety of new security protections. The strong sandbox of the BlastDoor service prevents the exploitation of a privilege escalation vulnerability after compromising the BlastDoor process. Whenever a message arrives in iMessage, it will pass via several security protocols that scan for malicious codes or links in the incoming message before allowing Apple’s push notification service to display the message.
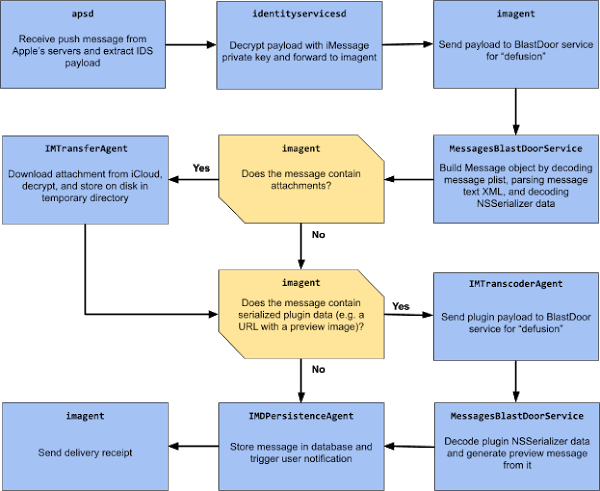
“The sandbox profile is quite tight. Only a handful of local IPC services can be reached, almost all file system interaction is blocked, any interaction with IOKit drivers is forbidden, outbound network access is denied. With this change, an exploit that relied on repeatedly crashing the attacked service would now likely require in the order of multiple hours to roughly half a day to complete instead of a few minutes. Overall, these changes are probably very close to the best that could’ve been done given the need for backwards compatibility, and they should have a significant impact on the security of iMessage and the platform as a whole,” Grob added.
Related Story: Why Apple Dropped macOS Big Sur Feature ‘ContentFilterExclusionList’










