
Security researchers identified a supply-chain attack targeting the Vietnam Government Certification Authority (VGCA) that compromised the agency’s digital signature toolkit. According to an investigation from the security firm ESET, cybercriminals exploited the software installers hosted on the VGCA’s website “ca.gov.vn” to inject spyware known as PhantomNet or Smanager.
The Vietnamese government has mandated the use of digital signatures and digitally signed documents. The VGCA is the authorized certificate provider. It also develops and distributes a digital signature toolkit and offers cryptographic certificates used to sign documents.
The “SignSight” Attack
The researchers named the cyber operation as SignSight attack, which occurred from July 23 to August 16, 2020. ESET researchers stated that cybercriminals modified two software installers, “gca01-client-v2-x32-8.3.msi” and “gca01-client-v2-x64-8.3.msi” for 32-bit and 64-bit Windows systems, which are available for download on the agency’s website. Attackers manipulated the software and added a backdoor to compromise users of the legitimate application.
“We were able to confirm that those installers were downloaded from ca.gov.vn over the HTTPS protocol, so we believe it is unlikely to be a man-in-the-middle attack,” ESET researchers said.
The URLs that redirected the users to malicious installers include:
https://ca.gov[.]vn/documents/20182/6768590/gca01-client-v2-x64-8.3.msi
https://ca.gov[.]vn/documents/20182/6768590/gca01-client-v2-x32-8.3.msi
PhantomNet Supply-Chain Attack
The users could get affected by PhantomNet spyware if the compromised software hosted on the official website is downloaded and installed on the targeted system. Once installed, the altered software hides its malware and runs the PhantomNet backdoor that tricks users as a regular file named “eToken.exe.”
The Attack Flow
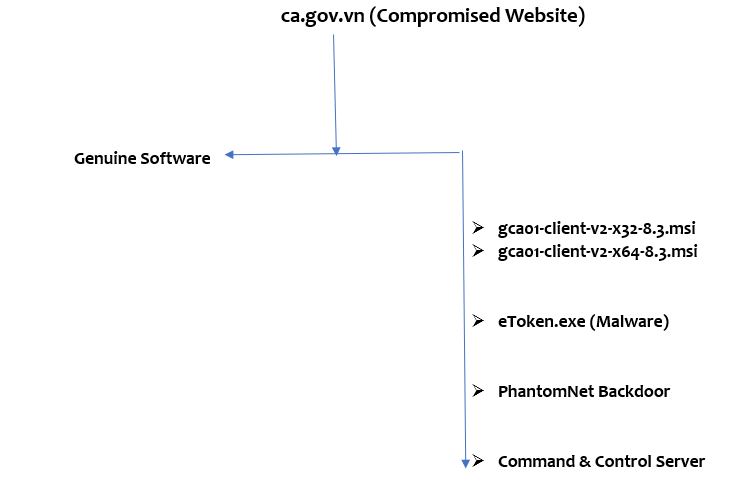
“We believe that the website has not been delivering compromised software installers as of the end of August 2020 and ESET telemetry data does not indicate the compromised installers being distributed anywhere else. The Vietnam Government Certification Authority confirmed that they were aware of the attack before our notification and that they notified the users who downloaded the Trojanized software,” the ESET researchers added.










