Despite the continuous security improvements, the concern over insider threats seems to be growing for organizations globally. The new distributed working conditions have also added fuel to existing fears. Even though most organizations stretched their security beyond their office...
Earlier in the week, the White House had acknowledged that a Russian state-sponsored group known as the Cozy Bear or APT 29 carried out targeted cyberattack on several U.S. Government agencies. Other than this, the hack is believed to...
Identifying cyber threats and anomalies is like finding a needle in a haystack. It is safe to say that with advanced persistent threats (APTs) in the picture, the needle stays where it was, only that the haystack has multiplied...
Cybersecurity experienced multiple challenges in 2020. Rapid digitalization and the new normal — work from home — brought new opportunities as well as risks. Cybercrime is maturing, and hackers are capitalizing on the pandemic by compromising health care institutions...
The White House on Sunday acknowledged reports that a group backed by a foreign government carried out a cyberattack on the U.S. Department of Treasury and a section of the U.S. Department of Commerce. As per a report from...
Security experts found a new “PLEASE_READ_ME” ransomware campaign distributed from the U.K.-based IP addresses targeting unsecured MySQL servers online. According to the researchers from Guardicore, the ransomware preys on weak credentials and has exploited around 83,000 victims and 250,000...
From a local food retailer to a multi-national company, ransomware attacks continue to loom over cyberspace. Ransomware operators target victims by encrypting their sensitive files, paralyzing operations, and demanding high ransoms. They also threaten victims by posting the stolen...
The CISO MAG Cybersecurity Crusader of the Year recognition honors the most influential personalities in cybersecurity. They have, over the years, been committed to bringing awareness into the realm of cybersecurity – to whom the information security industry is...
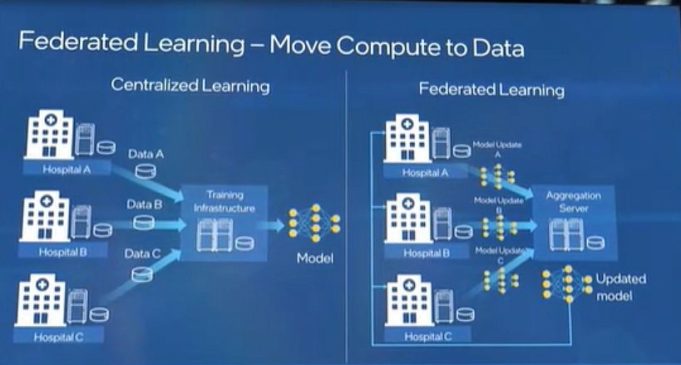
In many fields like medicine and financial services, the owners of data are bound by regulatory restrictions around data privacy. That can be a real inhibitor to bringing larger data sets together, which in turn limits how much we...
Sodinokibi ransomware has been wreaking havoc across the globe, hitting high-profile targets like CTAG, one of Europe’s leading automotive research centers, and a housing association in the U.K. Sodinokibi ransomware is currently ranked as one of the most widely...